I'm trying to resolve a problem with transfering large files between two datacenters. One is behind a Sophos SG-230 appliance, the other a VM running the Sophos image (both on latest firmware 9.501-5). There's an IPSec VPN connecting the two sites, both have GB Internet connections, thanks to the datacenters they're located in.
The problem is that when I'm transferring a large database backup file ( > 10GB ), via one of several protocols, it seems to be choking off other traffic, in particular SQL queries over port 1433 from one data center to the other, resulting in execution timeouts, and it starves the MS Remote Desktop protocol, causing me to lose access to the machines during these large copy jobs.
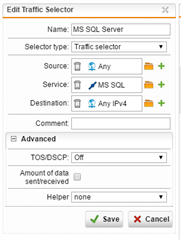
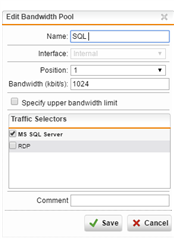
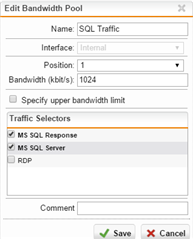
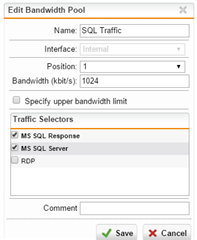
There isn't a lot of this SQL traffic, so I went through the QoS setup to define a traffic selector for MS SQL Server traffic (TCP 1433/1434), then setup a Bandwidth Pool for that traffic selector, giving it 1024 kbps (our SQL Server is seldom handling more traffic than that). I enable that bandwidth pool, and enable all of the NICs in the QoS/Status page -- I do this in the Firewalls at both sites.
Initiating the large file copy, through FTP, for instance, still results in a large number of SQL Timeouts.
I also loose RDP connectivity between sites when the large copy is running, so I tried setting up a similar QoS rule for MS Remote Desktop (TCP 3389), but it also still gets knocked out during the transfer.
This is making me think that I'm misreading/misunderstanding how QoS is really supposed to work.
My understanding was that doing what I've described above would result in reserving 1Mbit/sec of traffic space for SQL and 1Mbit/sec for RDP, out of the available 1Gbp/sec available, leaving plenty of space for my undefined/unshaped traffic (e.g. FTP/DFS/SMB etc...).... but it's just not behaving as expected.
Can someone set me straight on this?
Thanks!
This thread was automatically locked due to age.