Hi
UTM 125 and AP55 AccessPoints here.
I would like to put the AP55 Access Points in a seperated VLAN (Layer 2 Switches available).
But I am already failing one step ahead, did not getting any ip adress of the DHCP Server.
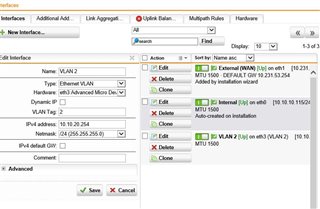
I have created an Ethernet VLAN 2
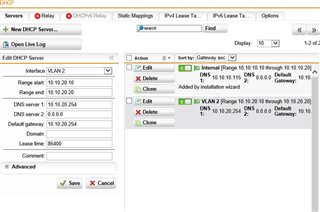
DHCP Server in this VLAN
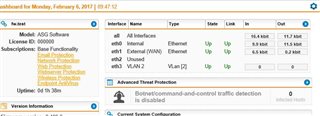
and a Win10 client plugged into eth3
Interfaces are up:
But even if i configure my NIC the static ip range in this VLAN i cannot reach the gateway and there are obviously no packets transmitted.
Tried this on the UTM 125 Appliance and in my Testlab with the UTM virtual appliance. What am i doing wrong!?
Thanks
Tino
This thread was automatically locked due to age.