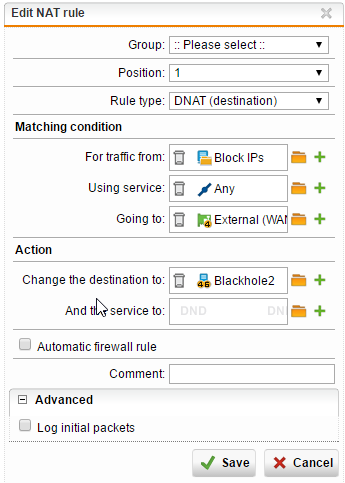
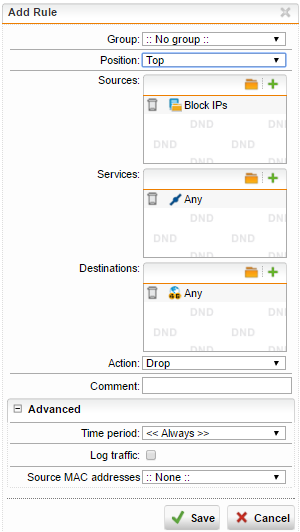
Here's the situation first. I get emails about all port scan notifications and intrusion alerts from our UTM. For the past 24 hours, this one IP address is port scanning us like crazy and then going on "likely SQL injections." So I thought, OK, I'll create a DNAT blackhole rule.
Basically the rule is this: any traffic from malicious IP address going to our server (internal IP) gets remapped to a non-existing internal IP.
Then I put that rule prior to the NAT rules for that server.
Still I'm getting the email notifications. Maybe the reason is because the Intrusion Protection Service is going to catch these attacks/probes regardless?
Thanks for any feedback.
This thread was automatically locked due to age.