Hi everybody,
we have the UTM 9 as a VM.
From one day to another I'm not able to connect to the User Portal anymore.
- Version 9.406-3
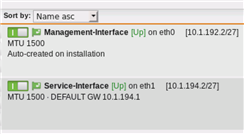
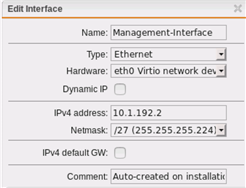
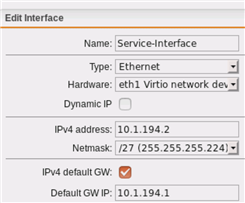
- Two interfaces (one for the Service (SMTP), one for (internal) Management)
- User Portal is listening on the Service Interface on Port 443 to "any"
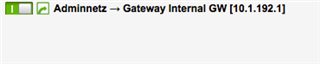
- Default Gateway is the Service Interface GW
I can see in the tcpdump, that there are packets leaving the correct interface (Service Interface) with the wrong IP (IP from the Management Interface).
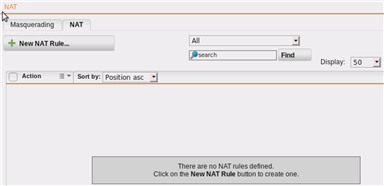
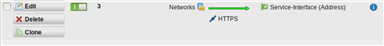
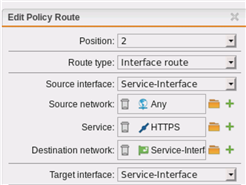
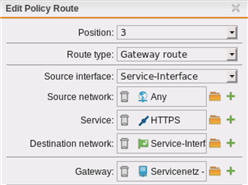
There are no NAT-Rules configured, but there is a policy route for HTTPS on the Service Interface.
Any thoughts?
Cheers,
Frank
This thread was automatically locked due to age.