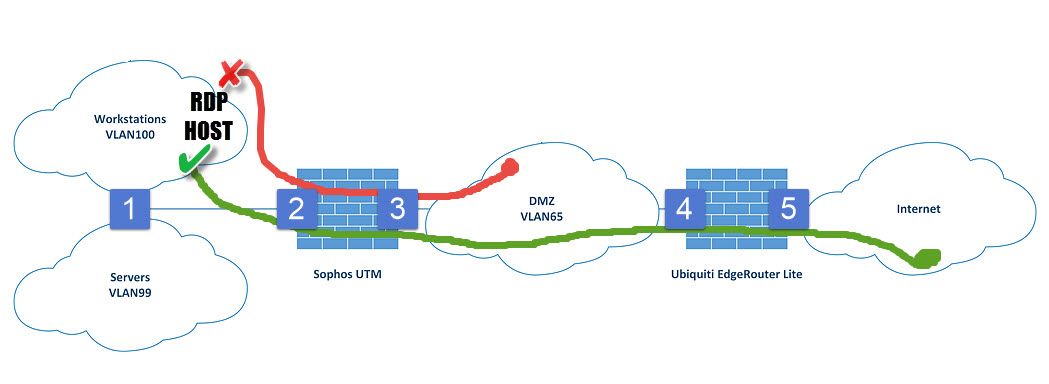
This is driving me CRAZY. Please help.
Public clients can access an RDP host in VLAN100, but DMZ clients cannot.
Why might this be so?
Note: DMZ clients have no problem accessing hosts in VLAN99.
Functional network diagram and notes below.
Thank you.
Workstations
192.168.100.0/24 VLAN100
GW 192.168.100.254 (switch)
Servers
192.168.99.0/24 VLAN99
GW 192.168.99.254 (switch)
DMZ
192.168.65.0/24 VLAN65
GW 192.168.65.250 (router)
Point1, switch (SVI):
192.168.65.254/24 VLAN65
192.168.99.254/24 VLAN99
192.168.100.254/24 VLAN100
default route 192.168.99.253
Point2, UTM internal:
192.168.99.253/24 VLAN99 GW NULL
Static route 192.168.100.0 mask 255.255.255.0 192.168.99.254
(created to allow VLAN100 hosts access to UTM webadmin)
Point3, UTM external:
192.168.65.253/24 VLAN65 GW 192.168.65.250
DNAT with automatic firewall rule to RDP host in VLAN100
Point4, router internal:
192.168.65.250/24 VLAN65 GW NULL
Point5, router external:
Public IP via DHCP
This thread was automatically locked due to age.