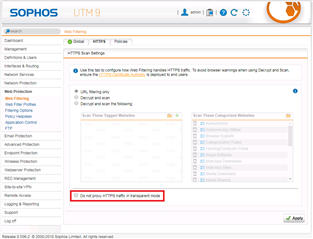
Is it possible that the check box that I have outlined in red below is labeled backwards:
Just as a matter of opinion, good UI should NOT include the word 'not' in the description of a check box. Additionally, I think this box should be labeled 'Proxy https traffic in transparent mode' anyway, because that is the way the UTM is acting, i.e. with the box checked https traffic is being proxied by the UTM in transparent mode and with the box unchecked https traffic is NOT being proxied in transparent mode. If the box is indeed labeled backwards it can cause a great deal of confusion.
thanks,
Richard
This thread was automatically locked due to age.