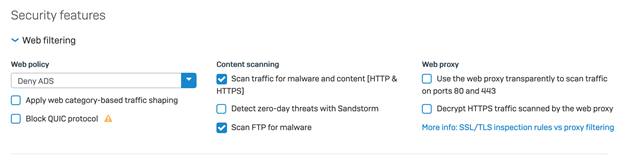
Exclusions to SSL/TLS inspection rules
XG Firewall provides default exclusion rules for websites and applications. These rules are positioned at the top of the SSL/TLS inspection rule table and are evaluated first. You can’t change their sequence in the rule table.
To the default exclusion rules, add only applications and websites that you don’t want to decrypt in any SSL/TLS inspection rule.
To exclude traffic from decryption using other criteria, you can create additional rules with action set to Do not decrypt and place them immediately below the default rules.
- Local TLS exclusion list: The list is empty by default. You can’t delete it from the exclusion rule. You can add domains to this list based on troubleshooting outcomes. Websites excluded through the control center or the log viewer are also added to this list. To edit this list, go to .
- Managed TLS exclusion list: Contains domains known to be incompatible with SSL/TLS inspection and is updated through firmware updates. You can, however, remove the list from the exclusion rule.
Exclusions by application: The list is empty by default. To add to the list, select the exclusion rule and add the Synchronized Security applications. Applications excluded through the control center are also added to the list.
Please document the differences between this new tab/option from exceptions available in Web > exceptions. Which one takes precedence?
Thanks