Table of Contents
Overview
This Recommended Read goes over how to troubleshoot WMI connectivity issues with Sophos STAS..
STAS uses WMI method for polling requests and Log off detection by default. STAS advance tab has the option to test WMI connectivity test for end-user IP.
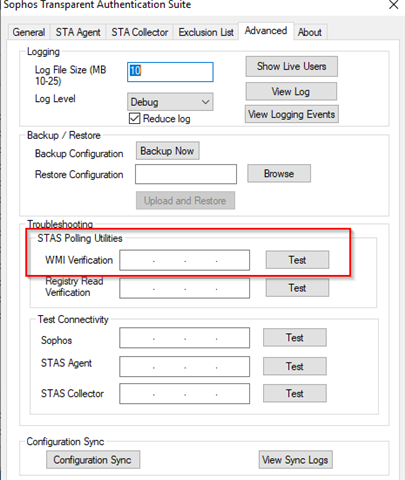
STAS uses setup credentials (provided during installation) to connect a remote computer for WMI.
Manually run WMI verification:
In some troubleshooting scenarios, the admin considers that the built-in WMI verification tool built-in on the STAS suite may not work as intended when the test returns with a fail status, which most of the case this isn't true.
The best way to take out of the way any chance of issue with the build-in WMI verification tool on the STAS is by running a manual WMI verification from the AD server itself using the native windows tool for testing WMI connectivity called "wbemtest".
Note: The admin has to recheck the STAS user access rights and password if the WMI query passes when the admin tries the manual test and fails when the admin makes the test connection from the advance tab.
Step to manually run WMI
Start wbemtest:
- select Windows -> Run
- When prompted for the Command to run, enter wbemtest
- Type wbemtest in Start -> RUN which will open WMI tester window.
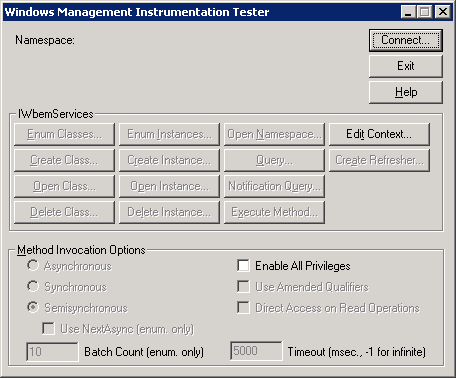
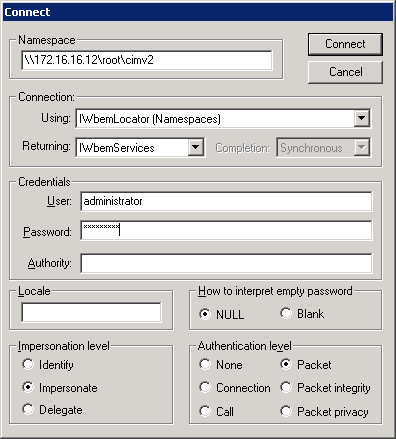
- Click Connect and type \\<Clinet IP>\root\cimv2 in namespace and type the domain administrator username and password to connect to the remote system over WMI.
- Click connect, if the remote device can connect over WMI it will show the tester screen
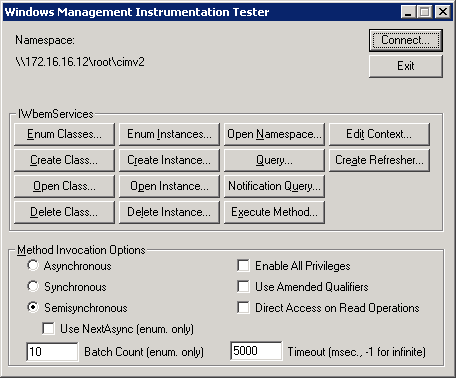
NOTE: in a Non-working condition the test results will look like this: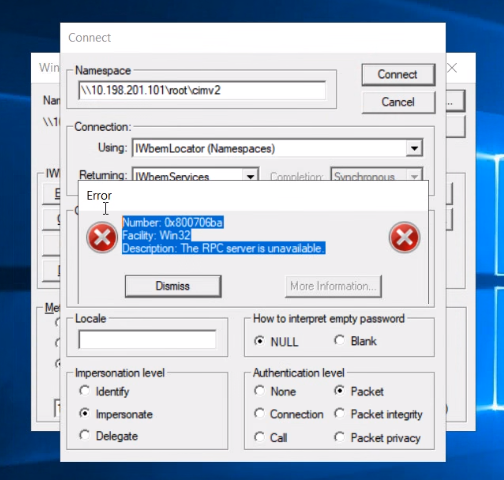
Click Query and type “select username from win32_computersystem”
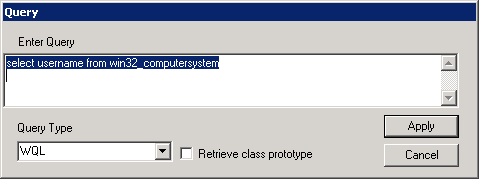
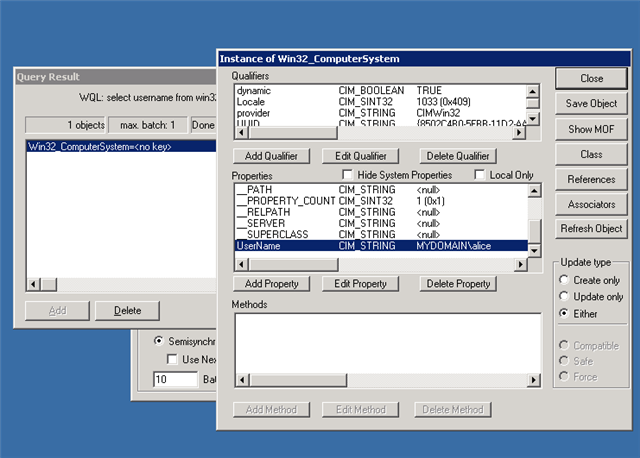
- Click Apply; it'll give you a query result, double-click on the result and it’ll open up a new window that shows the remote system username currently logged in.
WMI Failure Reason and some hit to make it work:
- Windows firewall and desktop antivirus need to be disabled for successful polling methods. Or need to add exceptions for ports 445 and 135.
- RPC, RPC locator, DCOM,WMI, remote admin services are enable
- The client device should resolve AD FQDN, if it isn’t able to resolve the FQDN add the following FQDN entry in the host file (C:\WINDOWS\system32\drivers\etc\hosts). Or Add AD IP as DNS and WINS in the client.
- If there’s any router in the path, make sure that ports 135 and 445 are open.
- AD can telnet on port 135 of the client device. If the firewall is turned on type this command to open 135
port : netsh firewall add portopening protocol=tcp port=135 name=DCOM_TCP135. - Ensure that the admin account used in the Collector has the correct admin permissions on the client's system
- Ensure DCOM remote launch permission is allowed. To check the permission Run
DCOMCNFG.exe
Click to Expand the Component Services folder and navigate to My Computer
Select My Computer and Right Click, the My Computer Properties window will open, click the COM Security tab and check the Launch and Activation Permissions - In order to avoid any WMI connectivity issues from the user computers, due to a Windows Firewall policy, Windows Administrators might configure a GPO policy to allow all connections from the AD servers to bypass any policy or setting that can compromise the AD server do WMI verification.
Updated Disclaimer
[edited by: Erick Jan at 1:49 PM (GMT -7) on 17 Apr 2023]

