Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Overview
With the Sophos Firewall v18, firewall rules, NAT and the outgoing WAN interface policy have been decoupled.
If you want to configure the Sophos Firewall v18 in MTA mode with two WAN uplinks, you can consider the following procedure as an example in order to avoid routing and email forwarding issues.
Here, we will consider a fresh Sophos Firewall install and configuration. Sophos Firewall will have two WAN uplinks, one on PortA and one on PortB.
MTA configuration will not be described in this article.
Applies to the following Sophos products and versions
Sophos Firewall v18
What to do
To configure the Sophos Firewall in MTA mode with two WAN uplinks, please consider the following steps.
- Don’t change the “Auto added firewall policy for MTA” under Rules and Policies > Firewall Rules.
- Verify that email traffic will not be intercepted by a firewall rule above the one at point 1, for example you can put it on top.
- If you want to use an IP address other than the WAN interface main IP address (for example an Alias – to be created on the WAN interface), we must modify the default Linked NAT rule to the “Auto added firewall policy for MTA”. Under Rules and Policies > NAT rules, please modify it as shown in the example below.
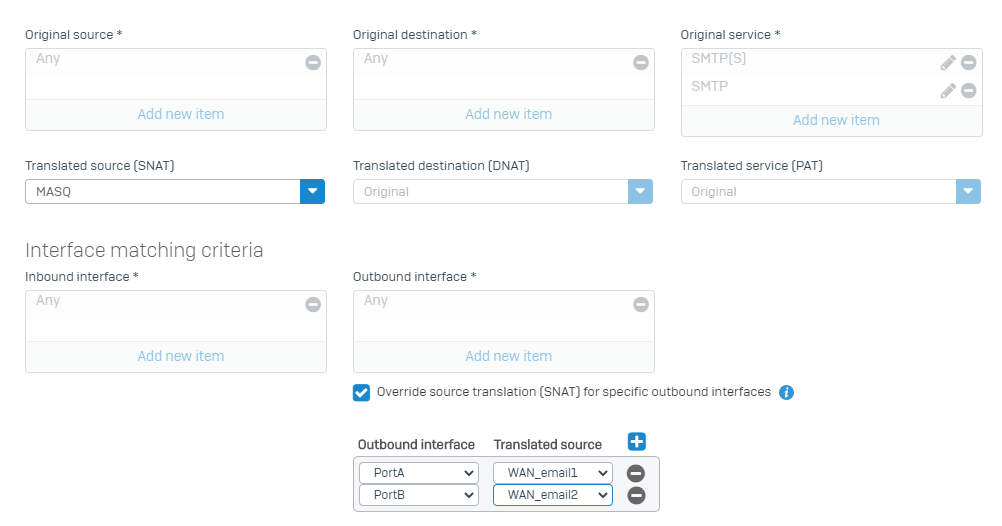
WAN IP addresses to use on each interface for outgoing email traffic are defined here by IP hosts with names WAN_email1 and WAN_email2. - Go to Routing > SD-WAN policy routing and add a new policy route as shown in the example below.
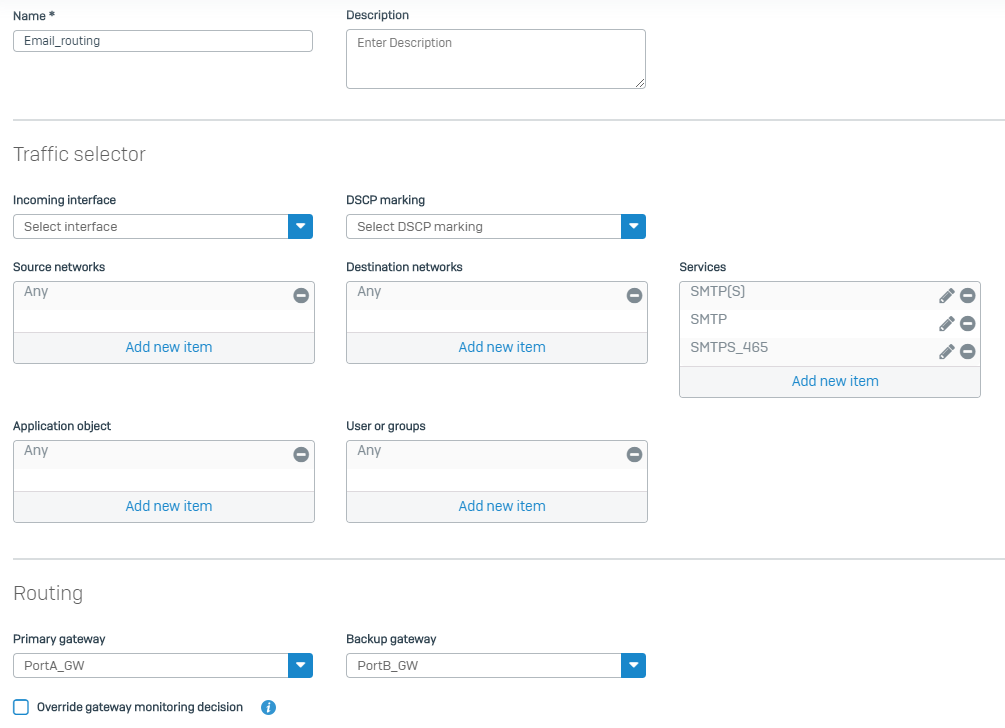
- With the described configuration, emails will be forwarded on WAN PortA with source IP address defined by WAN_email1. In case WAN uplink on port PortA will be unavailable, traffic will be sent out to WAN PortB with source IP address defined by WAN_email2.
Important note: When configuring SD-WAN policies for MTA email routing, please also verify global route preference settings: this document was written considering default configuration values. Please also consider that changing global routing priority settings might affect behavior for other configured services.
On Standard SSH console, you should have the following output for default priority settings.
console> sys route_precedence show
Default routing Precedence:
1. Static routes
2. SD-WAN policy routes
3. VPN routes
You can change them with command
console> system route_precedence set static sdwan_policyroute vpn
Related information
Updated Disclaimer
[edited by: Erick Jan at 12:12 PM (GMT -7) on 17 Apr 2023]

