Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
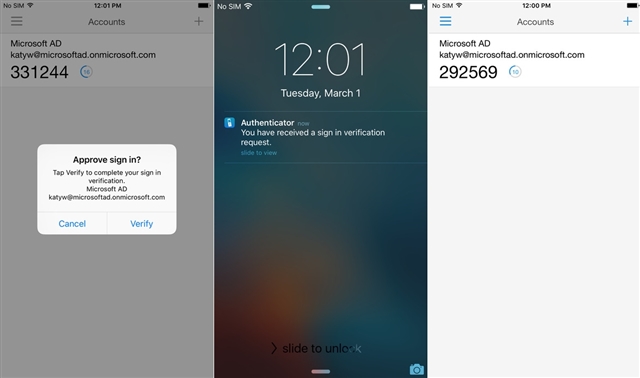
Some of the things that I’ve seen at work, is that Sophos Firewall VPN users are using one token for Sophos SSLVPN and another for ex. Office 365 services. Both tokens can be in Microsoft Authenticator, but only the one that Office 365 is using, can do the “pop-up”, letting the user easy sign-in, like this:
Nonetheless it’s easier for the IT dept. (and the user!) to maintain only one token solution [:)]
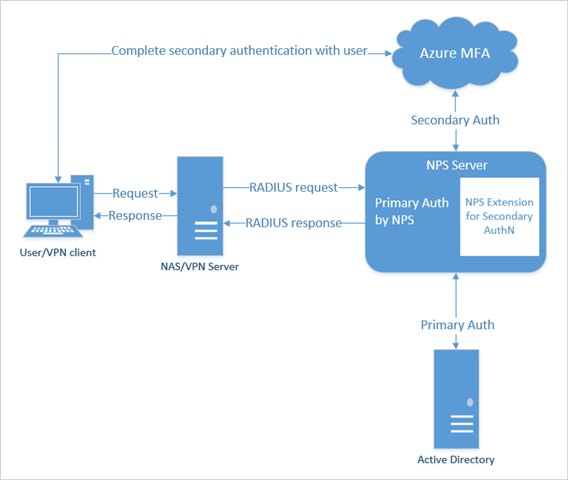
Here is the auth flow for Azure MFA with NPS Extension:
Nice isn’t it [;)]
So how to fix?
We setup Sophos Firewall for RADIUS validation for SSLVPN and UserPortal access, and if you use the built-in OTP solution, disable that [:)]
To get started:
- If you do not have MFA enabled for your Office 365/Azure AD account’s you can enable it through following link: https://aka.ms/mfasetup
- And of course you need to have set Azure AD Connect to get your on-premise talking with Azure, I will not go into the details with this here, as I assume this is already setup and working [:)]
Let’s go:
- Install the Network Policy Server (NPS) role on your member server or domain controller. Referring to the Network Policy Server Best Practices, then you will find this “To optimize NPS authentication and authorization response times and minimize network traffic, install NPS on a domain controller.” So we will go ahead and place this on the domain controller, but remember it’s also possible to do it on a domain joined member server!
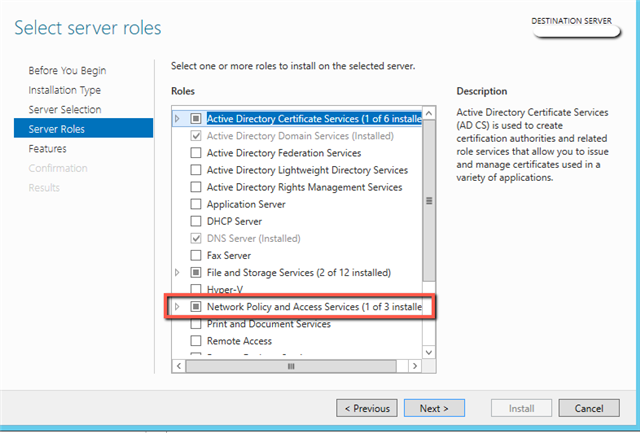
Press “Next” and the installation begins: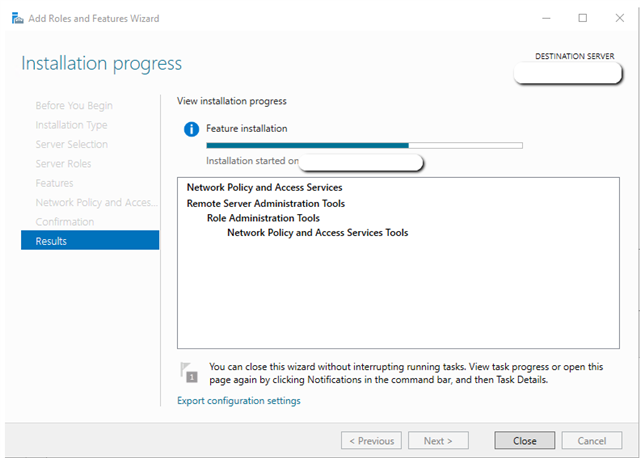
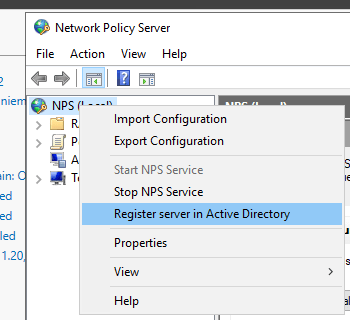
- After installation has ended, go and join the NPS to the Active Directory, right-click NPS (Local):
- Download and install the NPS Extension for Azure MFA here:
https://www.microsoft.com/en-us/download/details.aspx?id=54688
After it’s installed, go and follow the configure is like it’s stated here (Find TenantID and run Powershell script):
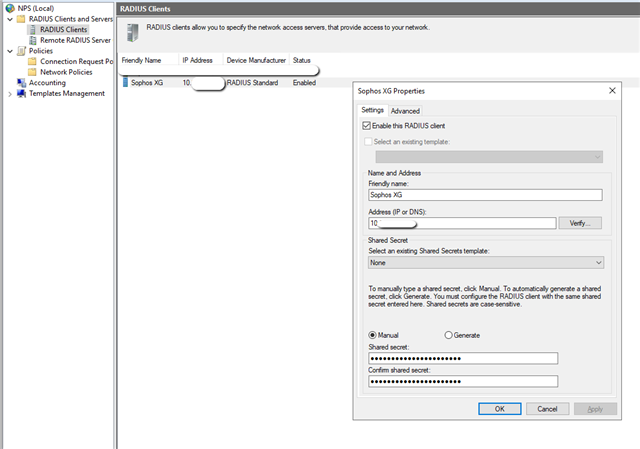
https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-nps-extension#azure-active-directory - Go and configure your radius Client, here it’s the Sophos Firewall:
Remember the secret, we need it later on [:)]
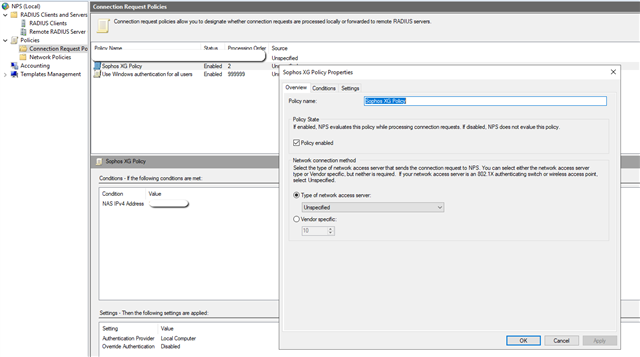
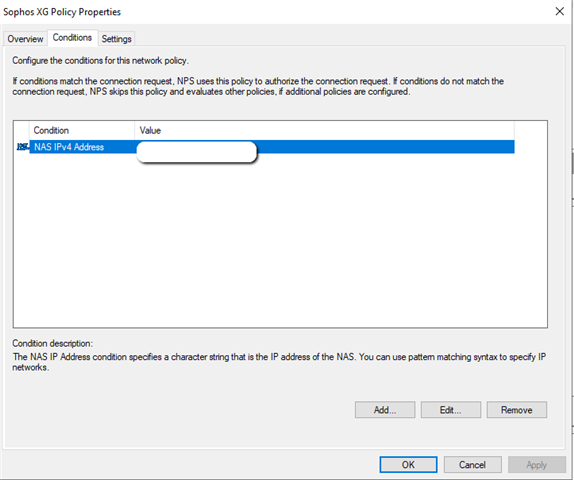
- Create a “Connection request policy”:
Type here the IP of the Sophos FirewallJust set like above, and the rest of the settings, just leave them to their defaults [:)]
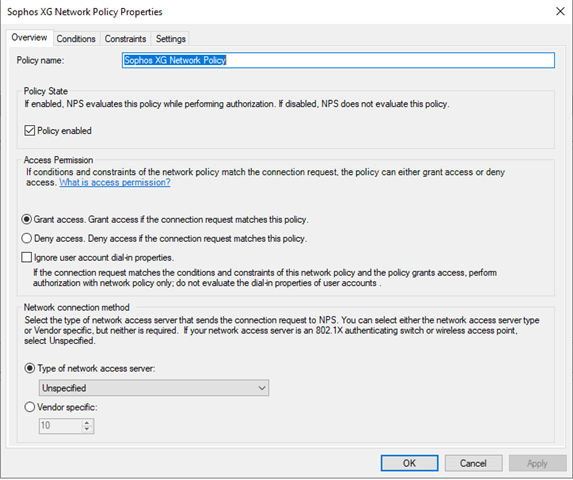
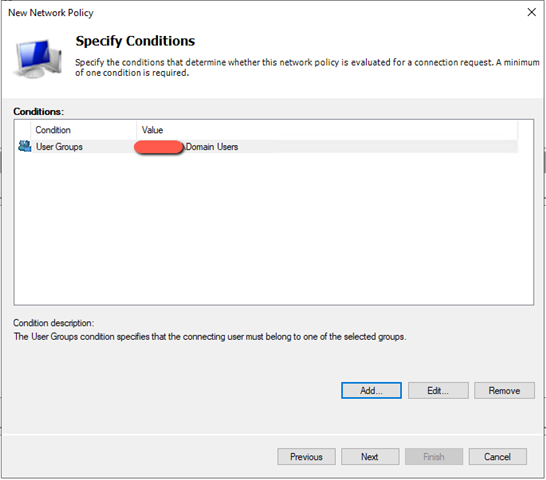
- Now create a “Network Policy”
Add a domain group, that shall have this access, to simplify, here I have choose domain\Domain Users
Now the EAP types, Sophos Firewall does only support PAP, as far as I have tested: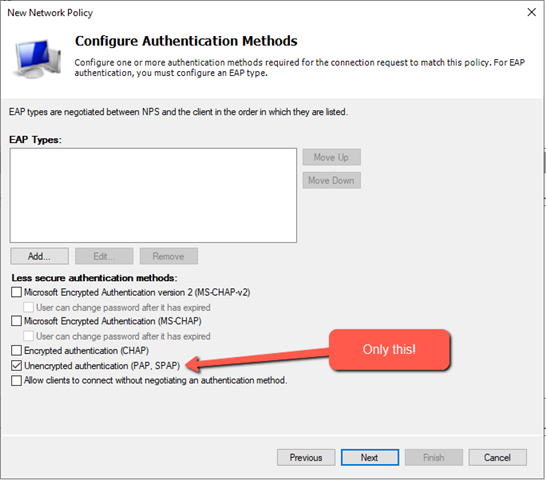
You will get a warning telling you that you have chosen unencrypted auth (locally – not on the Internet!), just press OK.
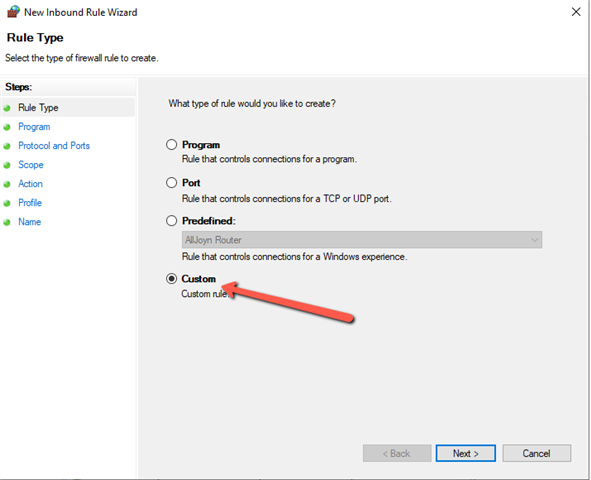
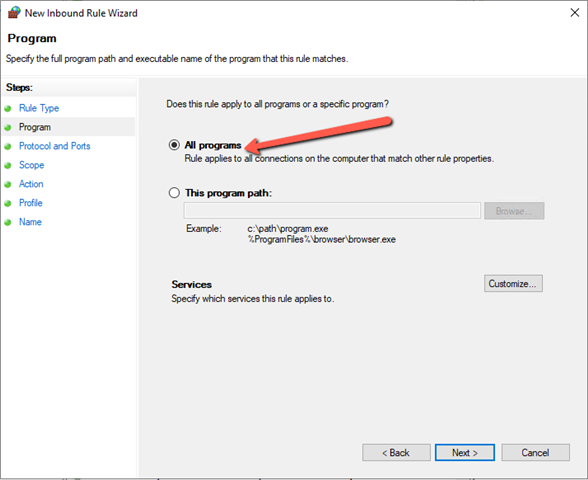
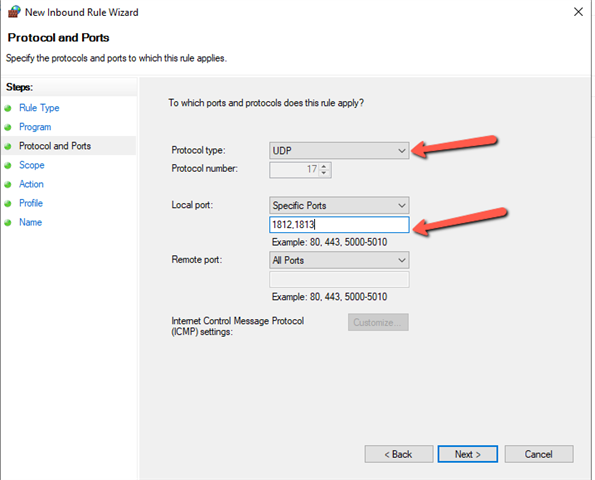
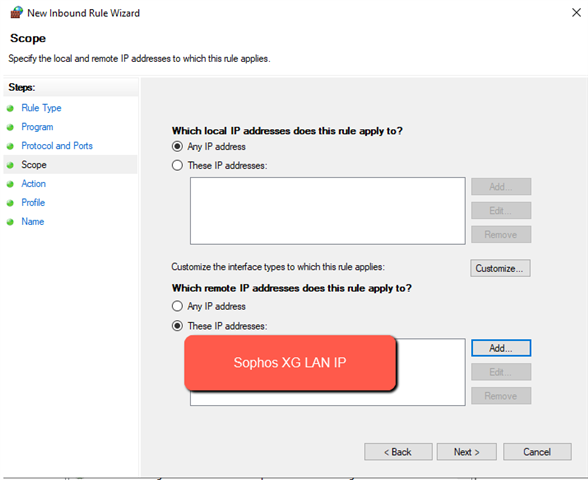
Just left the rest to their default’s and save the policy. - Now to create a firewall rule:
- Now to setup the XG for this:
Press ADD:
Remember to choose RADIUS:
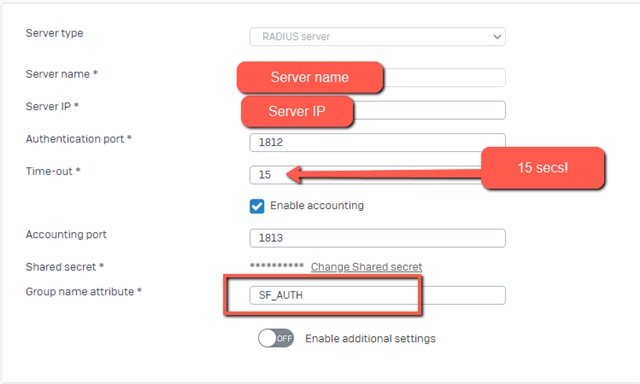
Fill in as your environment matches:
Type in the secret you wrote down earlier and create a host object for your NPS, also remember to change the timeout from 3 to 15 secs!
You can now test is the authentication through NPS and Azure MFA is working, change Group name attribute to “SF_AUTH”
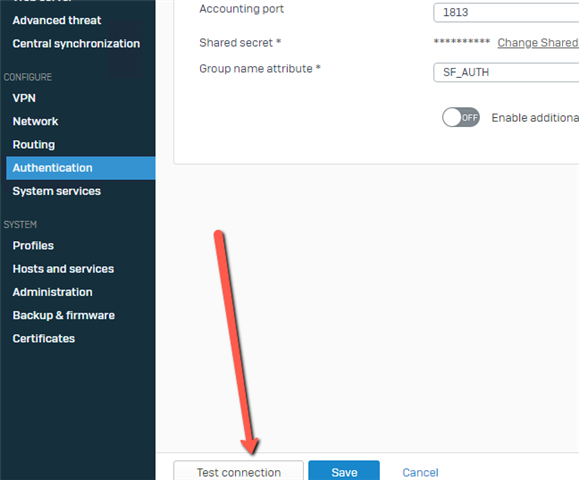
Press the TEST CONNECTION button:
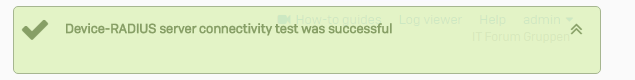
type in a users username (e.mail address) and password, and your phone should pop-up with Microsoft Authenticator [:)]
You should see this soon after you accept the token:
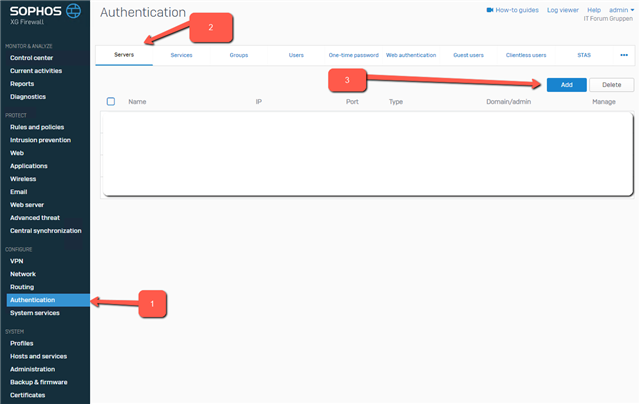
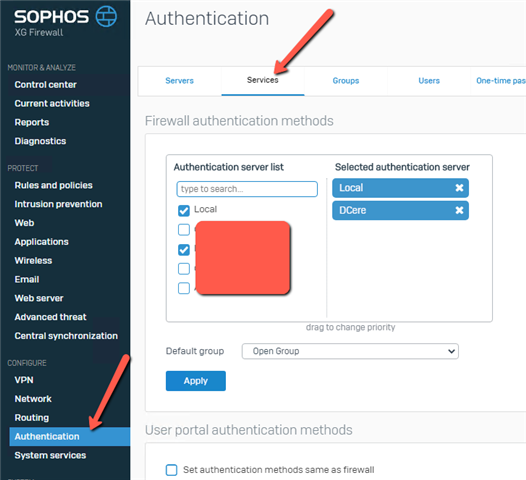
- Now head over to the Authentication –> Services section:
Add the new RADIUS server to:
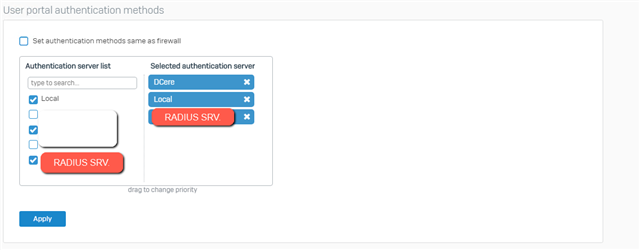
– User portal authentication methods
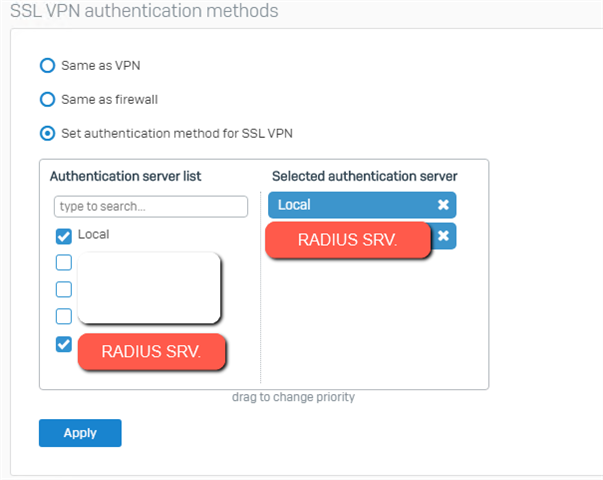
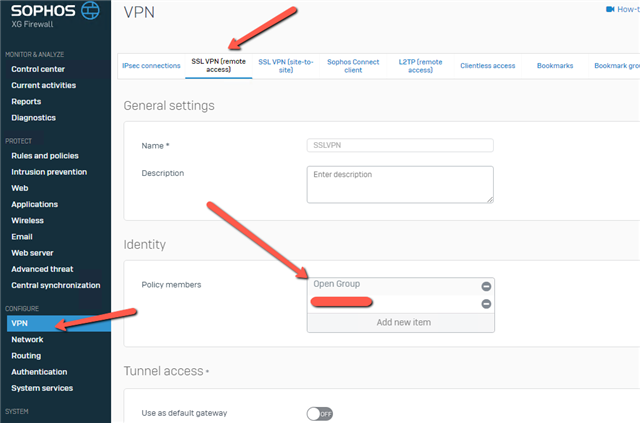
– SSL VPN authentication methodsAlso make sure that the group your AD / RADIUS users are in, is added to the SSLVPN profile:
- Now login to the User Portal and download a VPN client (You cannot use the old ones, if you already had those installed)
- Now connect through VPN, type in your full email in username and your password, then wait for MS Authenticator to pop-up, accept the token and you are logged into VPN [:)]
References:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-nps-extension-vpn
https://docs.microsoft.com/en-us/windows-server/networking/technologies/nps/nps-best-practices
https://community.sophos.com/kb/en-us/127328
Source: https://martinsblog.dk/sophos-xg-use-azure-mfa-for-sslvpn-and-userportal/
Updated Disclaimer
[edited by: Erick Jan at 1:46 PM (GMT -7) on 17 Apr 2023]