Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Hi all,
This Recommended Read goes over how to mass import objects using XML objects in the Sophos Firewall.
Table of Contents
Overview
As some of you might want to import multiple objects at once to the Sophos Firewall, there are simple tools in the field to convert a list to an XML File.
Exporting the Configuration
For example, I will use Notepad++ & the find & replace function within Notepad++.
Based on several guides on the internet on how to do so, we will start with the XML import/export option.
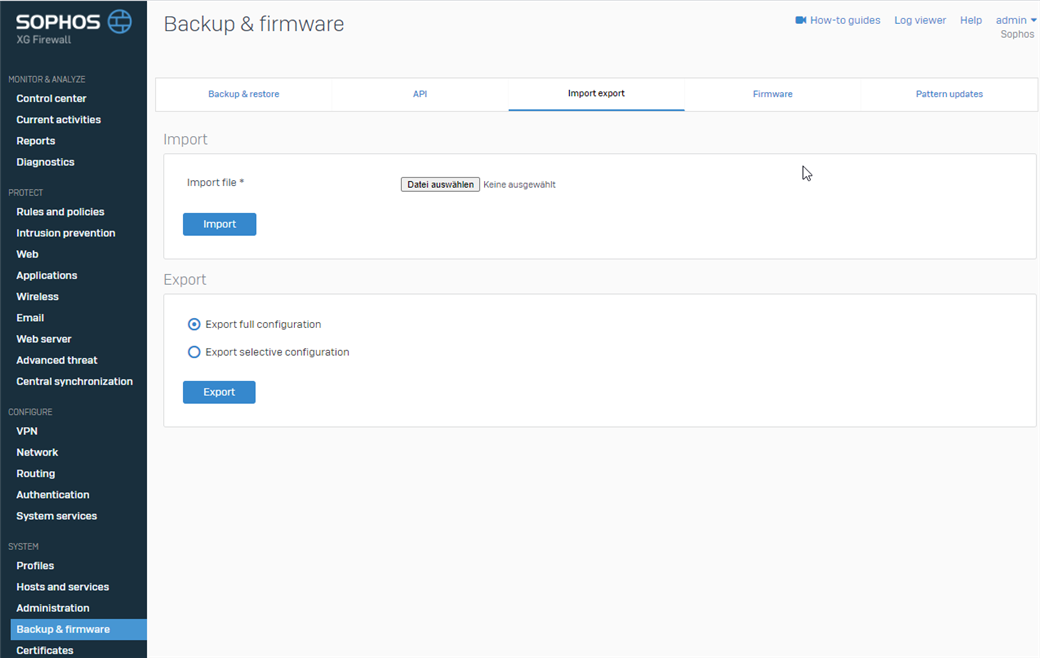
The XG Firewall gives us the option to export and import different configuration options in the GUI. You will find this in Backup & firmware > Import export.
This is the starting point of our task. As we want to import "FQDN objects" for example, we will export the current FQDN objects.
This can take some time to generate.
We are doing this to get the syntax that we need to use for the import later.
Editing the XML file
The result should be a file called: API-XXXXXXXXXXXXXX.tar. "tar" is another format of ZIP. https://en.wikipedia.org/wiki/Tar_(computing)
Using a ZIP tool (for example 7zip), we can decompress this file and get an entities.xml file.
Open this .xml file with your Notepad++ and you will get the correct syntax, which we need to import this file with new data.
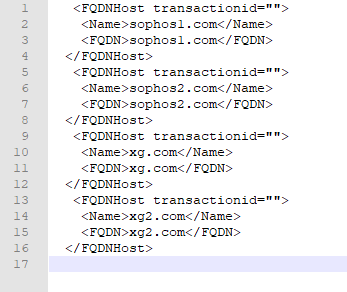
I'll now delete every entry except one to get the syntax correct.
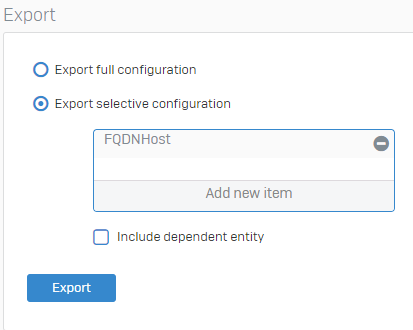
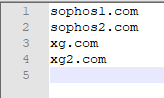
Let's take a look at our "raw" data, which we want to import.
I have prepared a list of 4 domains but this could actually be as big as you like.
Pressing STRG+F in notepad++ will open the search / replace mode.
This is another useful guide on how to do that: https://www.launch2success.com/guide/advanced-find-and-replace-in-notepad/
I will now do the quick mode for you.
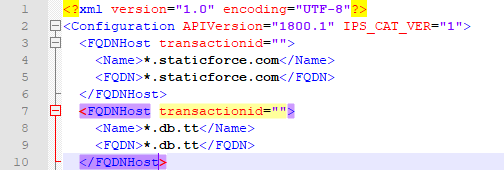
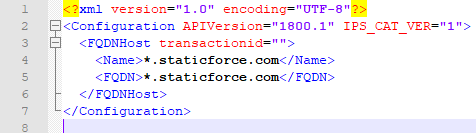
As your syntax dictates, an FQDN host needs to look like this:
<FQDNHost transactionid=""> <Name>*.staticforce.com</Name> <FQDN>*.staticforce.com</FQDN> </FQDNHost>
In Notepad++, we can actually select each entry and replace it with something else. The cool part about Notepad++ is, it can replace the entry and put the original content into the replaced content.
(German Screenshot):
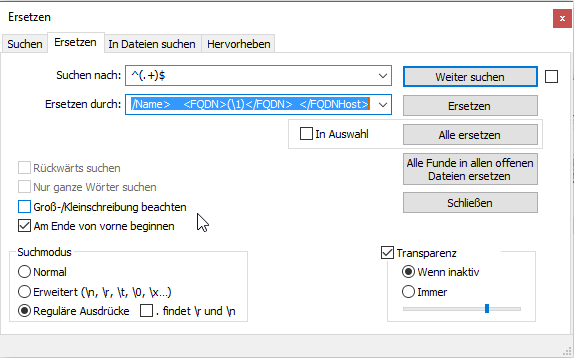
It's important to select the regular expression.
You will look for: ^(.+)$ <--- This will actually find each entry in each row.
And we are going to replace it with:
<FQDNHost transactionid=""> <Name>(\1)</Name> <FQDN>(\1)</FQDN> </FQDNHost>
It is the same syntax as above. But each entry has a (\1).
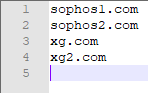
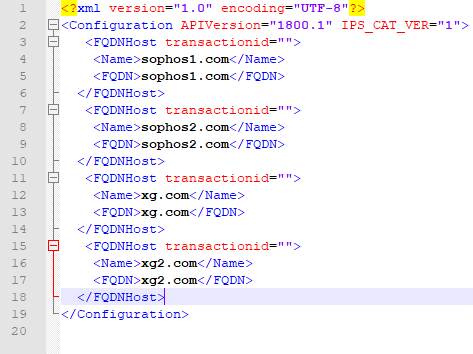
Putting this into place, let's replace each entry in our test:
This code will now be placed into the Entities.xml, which we had earlier.
Quickly save this file and place it back to the original API.tar File. (I am using 7zip for this).
Replace the current Entities.xml. You should notice, the change date should be the current time frame.
Importing the XML file
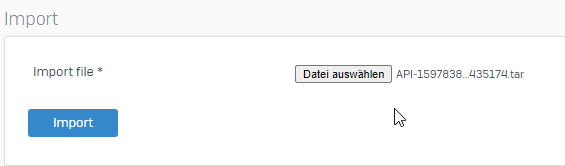
Back to the XG web admin. Now use this API.tar, which we updated and "import" this file.
The import can take some time, depending on the size of your API File.
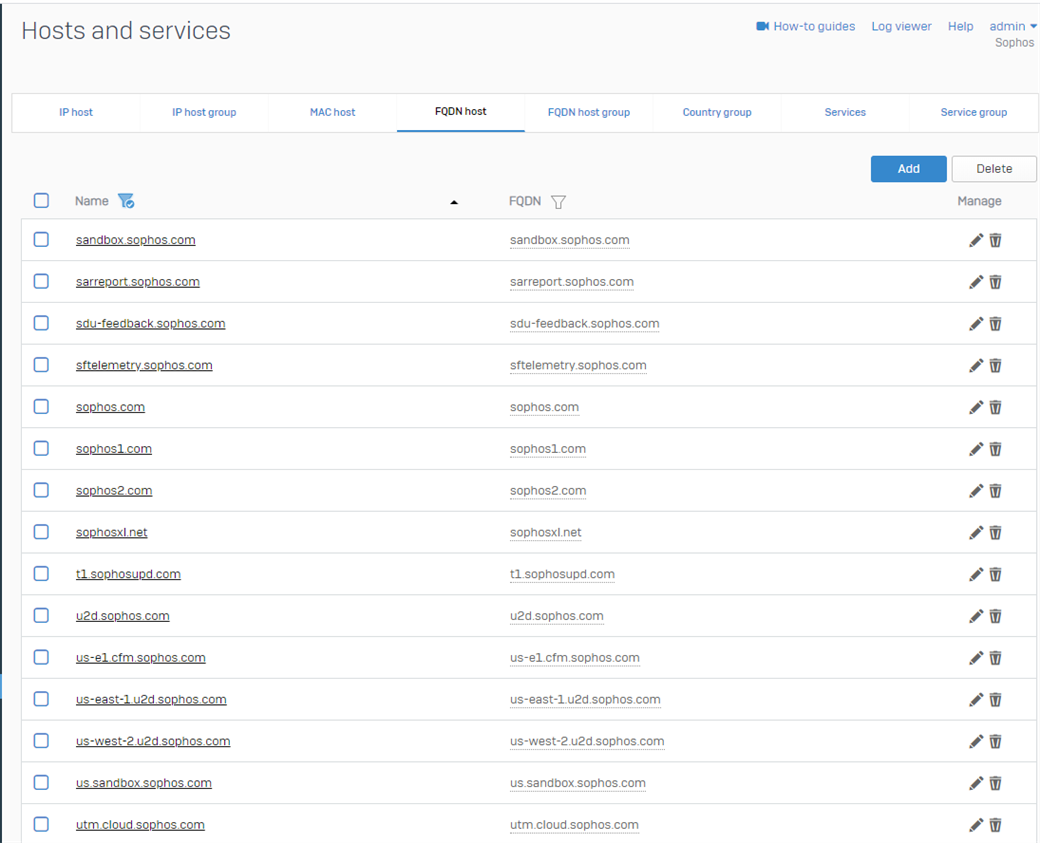
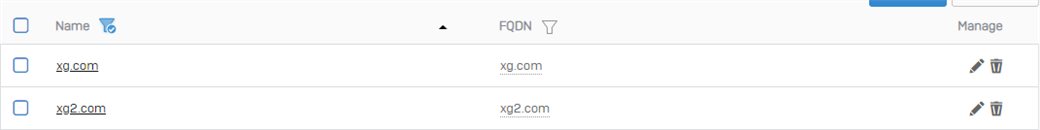
After the import, let's quickly verify that everything is correct:
Perfect.
If you have an error, you can verify the import in the log file on the CLI.
Go to Advanced Shell > /log/apiparser.log. The apiparser.log will represent all imported objects.
You can do this for all sorts of configurations.
Simply redo the same steps as above: Get the syntax of the object, replace your raw data, and import this new data into the XG Firewall.
Feel free to share your replacement Syntax, if you have any.
Updated Disclaimer
[edited by: Erick Jan at 9:14 AM (GMT -7) on 17 Apr 2023]