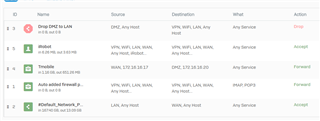
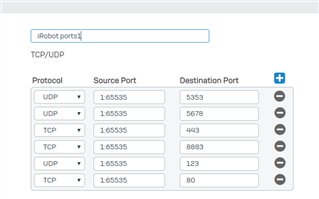
After some research, it seems the UTM version of Sophos has a fix for this as explained here https://community.sophos.com/products/unified-threat-management/f/general-discussion/93981/sophos-utm-9-and-irobot-roomba-980-port-8883/360479#360479
However, for the XG version, I am unable to SU to root and make changes as described above. Are there other instructions to make Roomba's communicate successfully with Sophos XG?
This thread was automatically locked due to age.