Hi There,
it seems that we ran into a mission impossible....
after we changed in a head office from Cisco 881 to a Sophos XG 135 with SFOS 17.0.3 we are unable to establish a IPsec Site to Site Connection to a Branch Office with a Cisco 866. Other Site to Site Connections (Sophos XG 105 and a Cisco 851) are working fine.
We tried to use the IPsec configuration from the cisco 851 but no connection. The Message at the Sophos is "received IKE message with invalid SPI (48AB99F0) from other side" with Status Deny.
The configuration at the Cisco 866 is as follows
crypto isakmp policy 1
encr aes 256
hash md5
authentication pre-share
group 5
crypto isakmp key "presharedkey" address ww.xx.yy.zz
crypto isakmp invalid-spi-recovery
crypto isakmp keepalive 10 3
!
!
crypto ipsec transform-set ESP-AES128-MD5 esp-aes 256 esp-md5-hmac
mode tunnel
!
!
!
crypto map SDM_CMAP_1 1 ipsec-isakmp
description ###Tunnel to Head Office###
set security-association lifetime seconds 86400
set peer ww.xx.yy.zz
set transform-set ESP-AES128-MD5
set pfs group5
match address 102
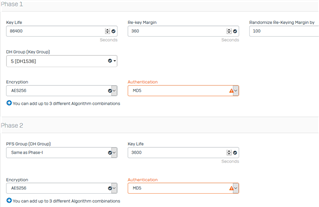
the ipsec profile at the Sophos XG 135 is
IKEv1
Main mode
Key Negotiation Tries 0
Re-Keying on
Because that is not working we tried IKEv2, SHA256, DH14 and so on but always the same errors. No solutions by searching Google helps.
at the Cisco Router the message at "sh cry isa sa" is "MM_KEY_EXCH" and then "MM_NO_STATE"
Does anyone knows someting about that?
The curious thing is, that teh S2S with the old 851 works....
Thanks for any suggestion and help.
Best Regards
Jürgen
This thread was automatically locked due to age.