Production Setup
- XG firmware = SFVH (SFOS 17.0.0 GA)
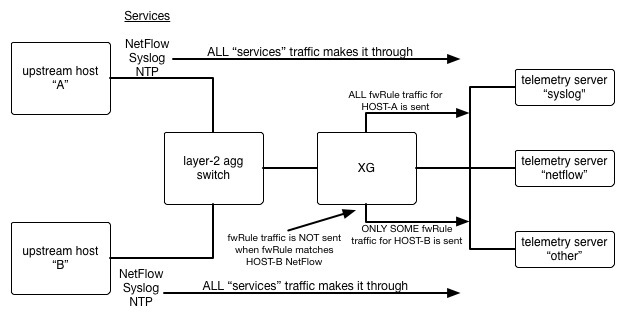
- Very high-level basic network diagram is included below.
- Variety of production FW rules that allow LAN --> WAN traffic. *** NOT RELEVANT to this issue ***
- Two upstream WAN-side hosts ("A" and "B" in the diagram) that are sending traffic for specific services down through the XG into telemetry servers on the LAN network.
- Two (2) production FW rules that allow traffic in the WAN --> LAN direction - one (1) rule each for hosts "A" and "B". As specified in the diagram, the services are (i) NetFlow; (ii) Syslog; and (iii) NTP.
- The only difference between these 2 fwRules is (a) source IP; and (b) NetFlow destination port #.
- All FW rules in both directions have the "Log Firewall Traffic" option ENABLED.
- Note in the diagram that the telemetry servers include both a NetFlow collector and a syslog server the latter collecting all syslog data including that sent by the XG when the "Log Firewall Traffic" fwRule option is enabled.
Test Setup
- Production environment as specified above PLUS the following...
- One (1) dedicated test fwRule (i.e. fwRule_underTest) cfg'd to essentially mirror the affected upstream host & service. This test rule is placed above the other two (2) WAN --> LAN production rules so it will be matched first. The rule is cfg'd as follows:
- Action = ALLOW
- Source zone = WAN
- Destination zone = LAN
- Source hosts\networks = HOST-B
- Destination hosts\networks = telemetry servers (NetFlow, syslog, NTP)
- Services = NetFlow (ANY --> UDP:17123)
- Log Firewall Traffic = Checked
- Everything else is left at default and\or disabled.
Issue
- Some fwRule related traffic that is supposed to be sent when the "Log Firewall Traffic" option is enabled is NOT being generated by the XG.
- This issue only occurs for a very specific situation - see Observations for more details.
Observations
- All services related traffic (NetFlow, syslog, NTP) for both hosts makes it through the XG and is received at the appropriate telemetry servers (see diagram).
- All fwRule related traffic from the unaffected host (HOST-A) is sent by the XG and received at the appropriate telemetry servers (see diagram).
- Only when the fwRule matches for NetFlow on the affected host (HOST-B) does the XG fail to generate the fwRule related traffic despite the "Log Firewall Traffic" option being enabled.
Verifications
- The fwRule_underTest counter steadily increases thereby indicating the rule is matching for NetFlow being sent from the affected host (HOST-B).
- HOST-B syslog data is PRESENT in the appropriate logfiles.
- HOST-B NetFlow data is PRESENT in the appropriate collector files.
- HOST-B clock shows in sync and being updated by the NTP server located on the LAN side of the XG.
- Packet captures taken at the LAN side of the XG do not have the fwRule related traffic that is supposed to be generated by the XG when NetFlow is sent from HOST-B thru the XG.
- These same packet captures do show the HOST-B NetFlow traffic as expected.
- These same packet captures do not contain any XG generated syslog packets that have a payload containing a "fw_rule_id" field matching the fwRuleId for the fwRule_underTest.
This thread was automatically locked due to age.