Hello all,
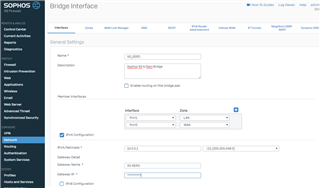
I have an Eero Pro mesh wifi system at home. I want to add an additional layer of protection and I have Sophos running in an ESXi VM on an appliance and would like to set that up in bridge mode. It is currently not deployed in bridge mode but I would switch it following this guide: https://community.sophos.com/kb/en-us/123098
I want to put the Sophos XG in front of the Eero so that the extra layer protects the wireless clients and not just the wired ones. If possible I would like to configure it like this:
<--INTERNET--> < --FIBER INTERFACE--> <--XG WAN--Sophos XG BRIDGE--XG LAN--> <--Eero WAN || Eero LAN--> <SWITCH>
<PUBLIC IP> <10.0.0.1> <10.0.0.2> || <10.0.1.1>
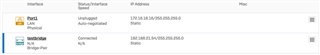
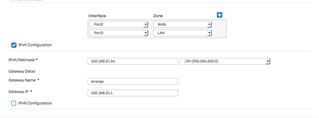
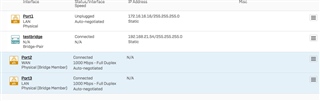
If I understand this correctly. The Sophos XG WAN port will pick up the Public IP from my fiber provider. I will then assign an IP to the XG bridge LAN port (ex: 10.0.0.1). The Eero WAN would get a static IP of (EX) 10.0.0.2. The Eero LAN I can do something like 10.0.1.1 and then set up a DHCP server on the Eero to provide IP's the rest.
I would love to run a /21 (.248) supernet so I can segregate my network into subnets down the road.
Thank you for your time
This thread was automatically locked due to age.