So very simple, generated a CSR and signed it with my CA, and uploaded the corresponding certificate & key to the Sophos. The cert uploads successfully as is shown in the "Certificates" page. I am now trying to setup a site-to-site IPsec VPN.
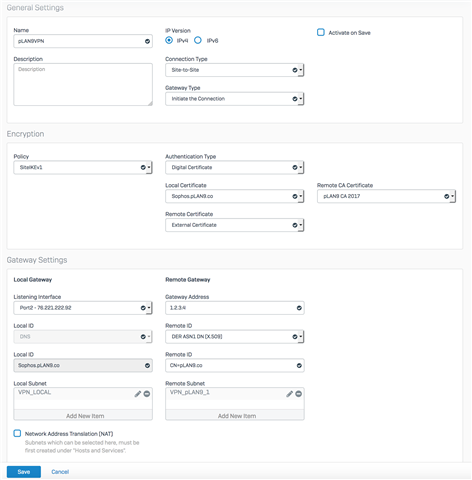
I add the local and remote subnets as host objects under the "Hosts and Services" link, and create the following IPsec configuration:
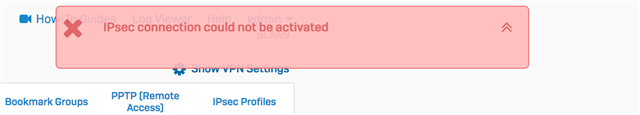
But when I try to activate it I get the following error:
It says "IPsec connection could not be activated". This is literally the most unhelpful error message I've seen in a long time..... wtf??
Why, exactly, can't it be "activated"? There is zero information in any of the logs. Before you ask, yes my cert is fine, I use the same CA and certificate request/signing process on dozens of routers with no problem whatsoever....... This is a XG85 with latest firmware 17.0.1 MR-1
Oh, and if you put that error message in quotes into Google, you get absolutely zero results on the entire internet, and the error is not listed in the documentation anywhere either....
This thread was automatically locked due to age.