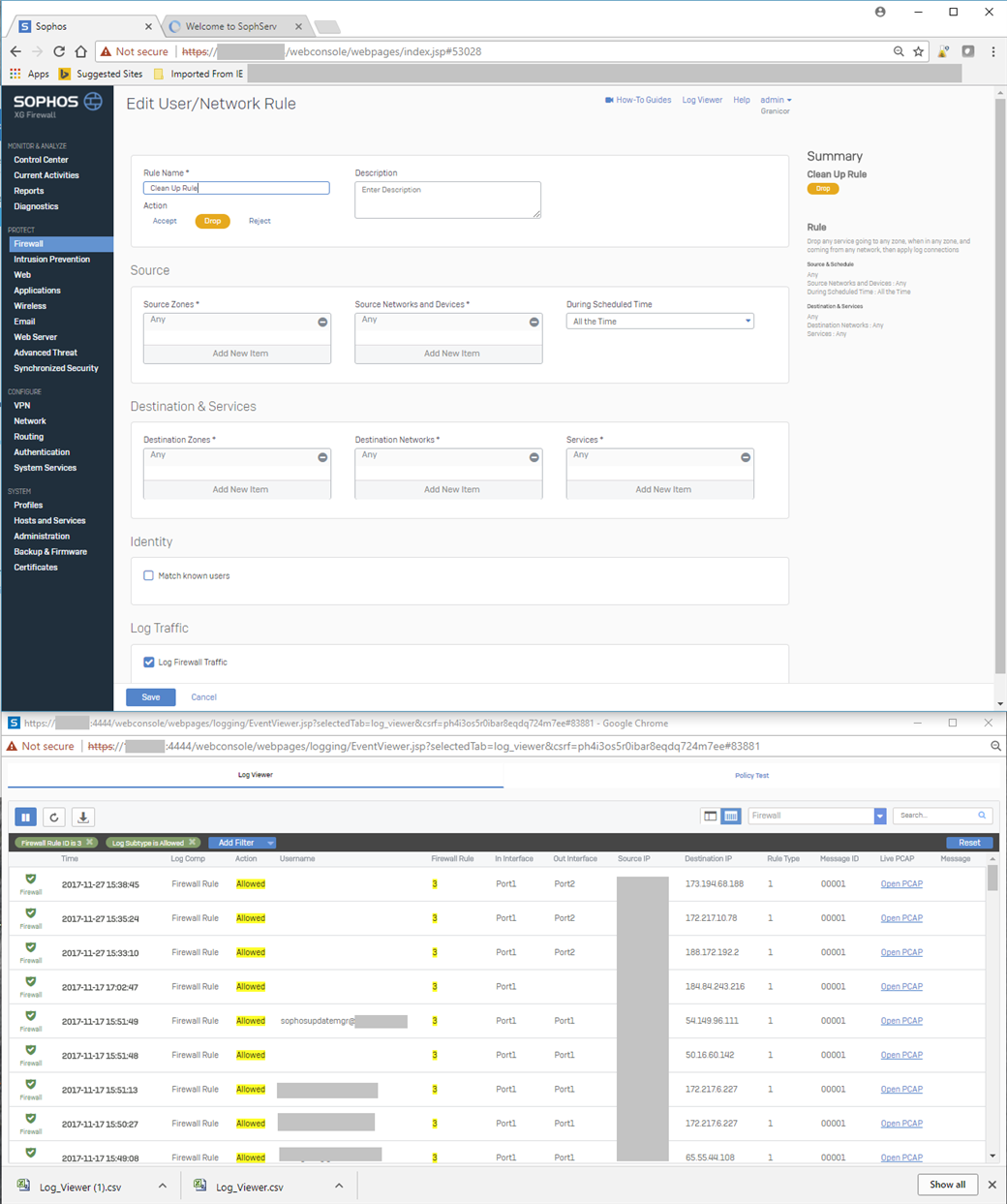
Hello Can anyone explain that to me ?
I have a clean up rule (no 3) "from any, to any, drop" that allows traffic on the Internet anyway !!!. See the rule and the log below.
Is it me, or this is a very serious issue ?
This thread was automatically locked due to age.