I will preface this by saying I had a UTM120 for three years with the UTM9 OS and right now thinking boy I miss those days. I was told that my appliance was nearing end-of-life so to renew licensing I went with the XG115. I had configured UTM9 on my own and generated help desk cases if issues arose. This appliance is quite a bit different. Firmware XG115 (SFOS 17.0.0 GA) so on the latest.
What I am trying to resolve right now is that any type of web surfing is extremely painful. I have an on-premise Exchange server so port 443 is being forwarded to it but I also have the default network rule of WAN to LAN all ports and all services are open. I have a similar network rule that WAN to LAN port 443 is open thinking of other workstations that initiate SSL traffic it will find its way back to the device that initiated the traffic. Let's face it. Most web sites are https. I am constantly being warned that the certificate cannot be verified and I have to click to still access the site or create an exception for the site depending on the browser. I cannot log in using an account to any web site. Some sites I can't even create the exception. I can't use the StartPage search engine. Amazon looks like crap. No pictures and just a bunch of links.
A little bit on the network. Uverse gateway goes to a Cisco ASA appliance that I consider my perimeter (and why not have another layer of defense !). The XG is in bridge mode. For a time I would go to my OWA site for my on-premise exchange server and would get certificate errors there to (not up for renewal for another two weeks yet). The ASA is listed as the Gateway for the XG in the WAN port. The Lan port on the XG was plugged into my SG300 Cisco Switch. I don't go too crazy with the security on the switch. Just the default VLAN1 with port security tied to the MAC address of the device using the port. This configuration worked well with UTM9.
I get the feeling that some of the traffic is getting recognized as DDOS or TCP Flooding and discarded judging by what I see in the logs. I did click on the setting for allowing dynamic routing on the WAN port. I also made the XG the default gateway for the network.
Windows update appears to work. I have slimmed down security until I figure out the issue. Not using IPS on any of the firewall rules yet. I can connect to my network via RDP, SSH, FTP, my IP Cameras, and other things which use Business Application rules.
Under Web > General Settings I deselected "Block Invalid Certificates" and then was able to use ADSM to get to my ASA Appliance otherwise that was a problem too. HTTPS Scanning Certificate Authority is on the default SecurityAppliance_SSL_CA. I know I had issues with this option on the UTM9.
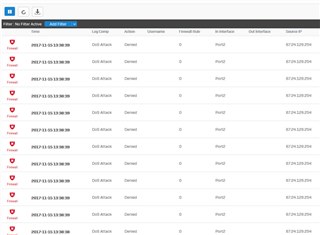
Firewall rules referencing rule 0 ?
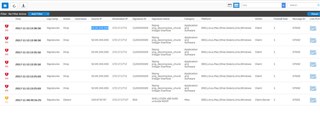
Most logs are empty but Firewall and IPS have a lot in them. This is IPS. This is cloudflare but willing to bet part of my trip to the Amazon Web Site:
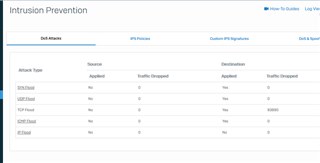
Notice TCP Flood and the number of packets dropped.....
I have other issues but this is priority # 1 ! If anyone has ideas I would appreciate your assistance ! Thank you.
This thread was automatically locked due to age.