Hi all,
I moved from a PFsense firewall to Sophos XG but I do not get the port fowarding to work. I would like to have access to my Synology DiskStation from the internet. I have the following setup:
DSL modem: 192.168.1.1
Sophos XG WAN IP: 192.168.1.2
Sophos XG LAN IP: 192.168.2.1
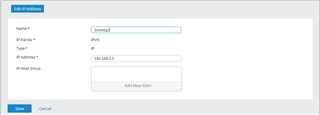
Synology DiskStation IP: 192.168.2.5 - Application running on Port 5001
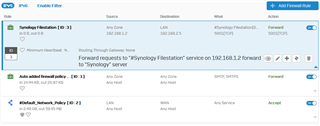
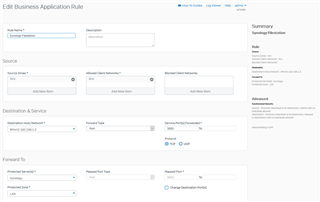
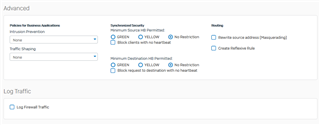
I have read a lot of threads in this community but I do not get access from the internet. Here is my firewall configuration:
Protected Server config:
Does anybody have an idea, what I am doing wrong?
Cheers
Robin
This thread was automatically locked due to age.