Dear experts,
I just got my Sophos XG Home license and installed it on a dedicated box.
I would appreciate some advice, how to set it up correctly in my enviroment.
My situation is as follow:
- Cable connection with 5 public, static IPs
(Actually its a /29 subnet, but one of the addresses is used as the ISPs gateway address) - I have a LAN with clients and some servers, that should only be accessible from inside my network
- some servers shall be assigned dedicated public static IPs so they can be reached from the internet (let's call it DMZ)
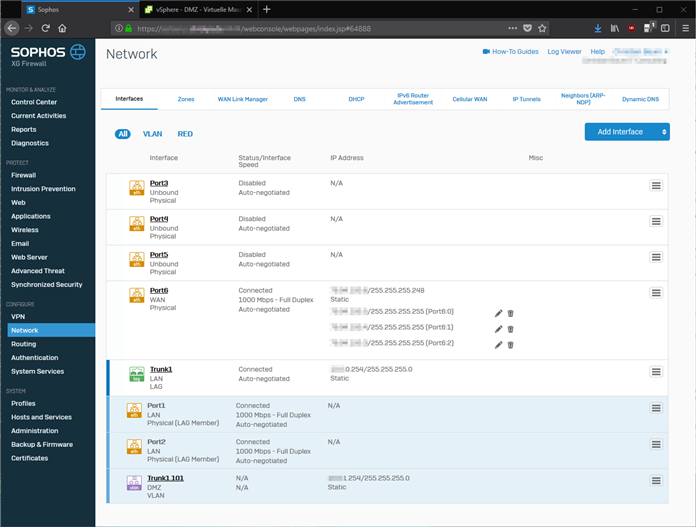
- all servers are running on a VMWare ESXi which is located in my LAN
- I'm using a manageable layer 2 switch (HP 1810 atm, ubiquiti US-24-250W in near future)
- i would like to use VLANs to separate the LAN from the DMZ traffic and prevent uncontrolled access from one segment to the other
- Later on I would like to be able to access my internal network via VPN (preferable using L2TP)
- I would like to setup rules for traffic between all segments (LAN, "DMZ" and WAN/Internet)
As I don't have access to the whole subnet (ISPs gateway in "my" subnet), a correct routing is not possible, right?
So my idea was to setup a bridge between WAN and DMZ and assign the subnet to it. The DMZ interface is a VLAN interface and it doesn't seem to be possible to add this to the WAN-DMZ-bridge in Sophos XG.
Second idea: I define one Port on the Sophos XG machine as the DMZ-Port and force-tag all traffic on the "DMZ switch port".
Are there any smarter / better / more secure ways to achieve my requirements?
What are your suggestions to implement the scenario described above?
Thanks a lot in advance.
Regards
Chris
This thread was automatically locked due to age.