Hi All,
I've had a bit of mare configuring and installing this recently - hence the plethora of questions over the past couple of days. Anyway, I've got to a new stage at the moment.
My network is configured as such:
DMZ 10.0.0.16/28
^
(To be known as WAN) I
Internet <--------> Sky Q Network <---------> Sophos XG <---------> Home Network. 192.168.0.0/24
10.0.0.0/28
First off, to try and answer any questions...
- The Sky Q hub is in place for 2 reasons:
- Because Sky uses something called MER to authenticate its routers against their network. This is a very uncommon method of connection that's used in place of PPPoE, as a result there are very few routers that can authenticate over it and I don't believe that the XG is one of them.
- Sky Q creates a mesh network in your house, all of the satellite boxes actings as rebroadcasts to each other improving your network WiFi coverage. Which is cool. However, they connect to each other over WPS which is very, very bad for security. This, unfortunately, is a non-optional configuration. For those of you that don't know WPS is a form of authenticating wireless devices via the push of a button. This then broadcasts a 0-9, 8-digit pin for other devices to connect to. Unfortunately, authentication over WPS cannot be turned off; so if your router is WPS enabled it means anyone with access to Reaver can get onto your network within a 12 hour period. So, given that Sky has to use this for its satellite boxes; I want to segregate my home network and DMZ away from this vulnerability. Unfortunately, it's a necessary evil.
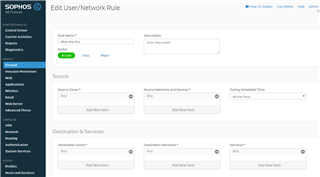
- My DMZ is hosting a number of Internet accessible services such as Plex. I want to stop the DMZ accessing the LAN except for the traffic I specify (firewall rules - something I need to configure later on)
- I want to block all traffic from the WAN (Sky Q) segment of my network accessing my LAN and DMZ; except for that coming directly from the Internet via my Sky Q gateway. (Firewall rules - later config).
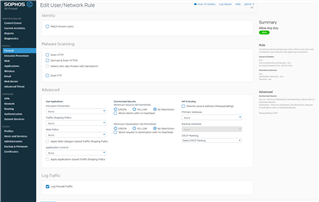
- I have tried the following firewall rules to get traffic to flow from my LAN out my WAN.
- Create specific firewall rule allowing traffic out, but not in (basically an attempt at the above).
- Create generic "Any->Any Allow" rule to allow all traffic for testing purposes - put this rule at the top of the list.
- Turn off all firewall rules.
- Since writing this; I have found this thread which seems to be a similar issue to mine. I'm not sure if i configured the "Match known users" segment but it's something I will check when I get home. Although given the fact that I turned off all Firewall rules; this should have negated this - unless the firewall is set to "block everything" if there are no rules.
- I created an omnicast rule that points all traffic (0.0.0.0/0) to my exterior Sky gateway 10.0.0.1/28.
- I can access the HTTPS configuration page from my LAN segment; traffic just appears to not be able to leave the network.
My questions are:
- Please help me get this working. Ask any questions you like.
- Does the firewall default to "block everything" if there are no rules defined.
- Apart from the "match known users" segment, is there anything else that you think could be causing this issue?
- Do I need to do anything with the routing/networking settings? Is my Omnicast rule a pointless and vein attempt to get it working?
Any help that you can provide would be greatly appreciated
This thread was automatically locked due to age.