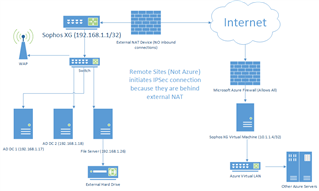
Hi, I've got a site to site VPN working and I can ping from either side but I don't see any option to route internet traffic as well as network traffic. I also couldn't find any documentation on the subject. If someone could please enlighten me on how to configure the routing for the VPN it would be much appreciated!
Thanks
This thread was automatically locked due to age.