Hi folks,
I'm stumped by the SSL VPN (remote access, not site-to-site) on my XG16 firewall. I've set it up, I think correctly, but the clients on both PC and Android stall just after verifying the certificate and fail to connect. There's absolutely nil in the XG logs, in spite of the VPN settings having "debug mode" turned on!
Anyone have any ideas?
Typical client log reads like this:
Resolve address - ok (gets the public IP of the XG box)
Contacting via UDP
Wait
Connecting via UDPv4
Tunnel options V4,dev-type tun,link-mtu 1602,tun-mtu 1500,proto UDPv4,comp-lzo,cipher AES256-CBC,auth SHA512,keysize 256,key-method 2,tls-client
Creds: Username/Password
Peer info: <version info etc of client>
Verify OK: depth=1
<certificate details for the root cert>
Verify OK: depth=0
<certificate details for my GeoTrust-issued cert on the XG box>
... 30 seconds or so go by...
EVENT: CONNECTION_TIMEOUT
EVENT: DISCONNECTED
----OpenVPN Stop----
The Android client is OpenVPN Connect with the OVPN file downloaded from XG's user portal; the Windows client is downloaded entirely from the user portal.
As I said, el zippo in the XG logs - no sign of firewall blocking anything, no IPS squeaks, nothing in the system log about VPN.
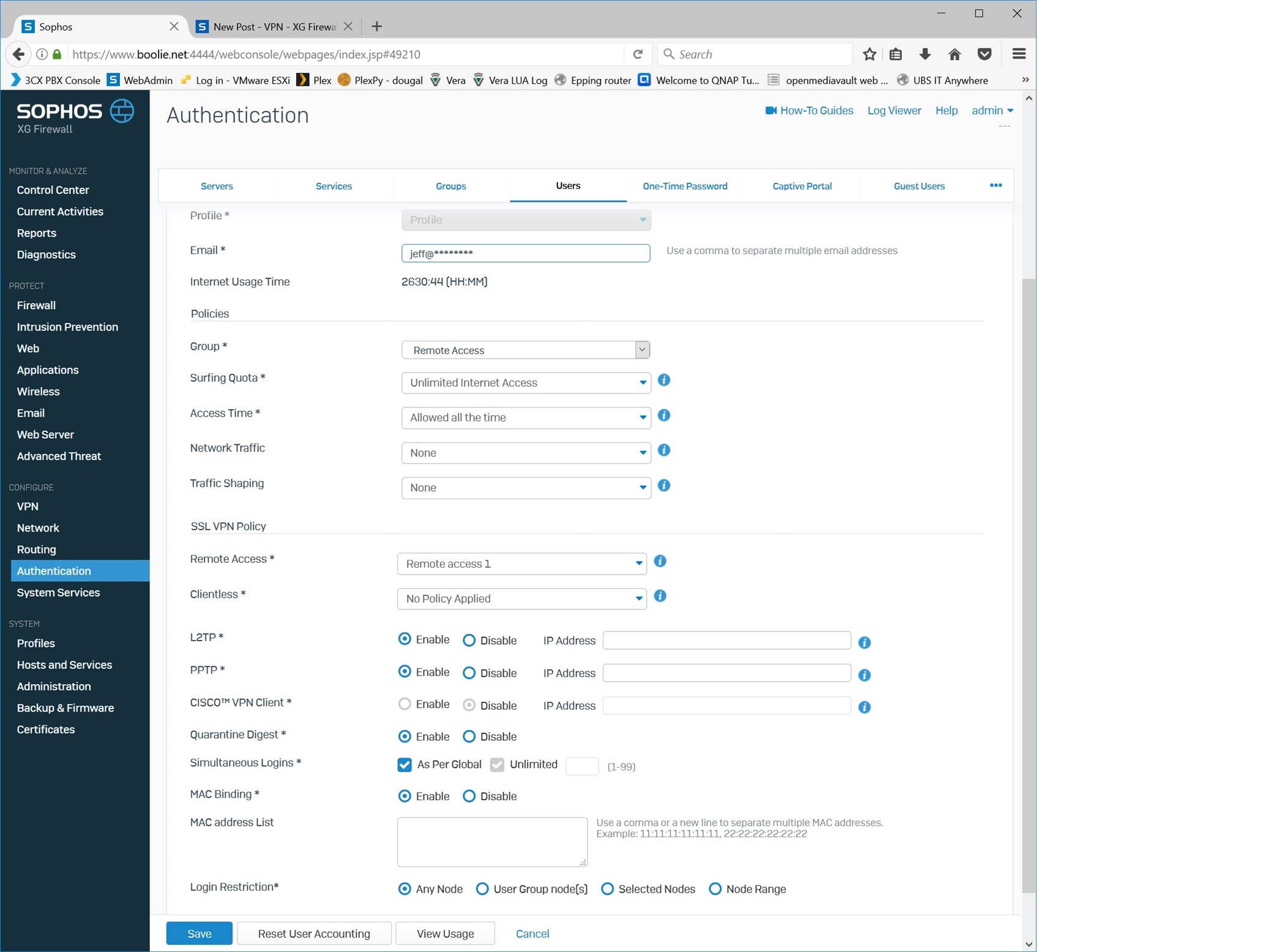
User config:
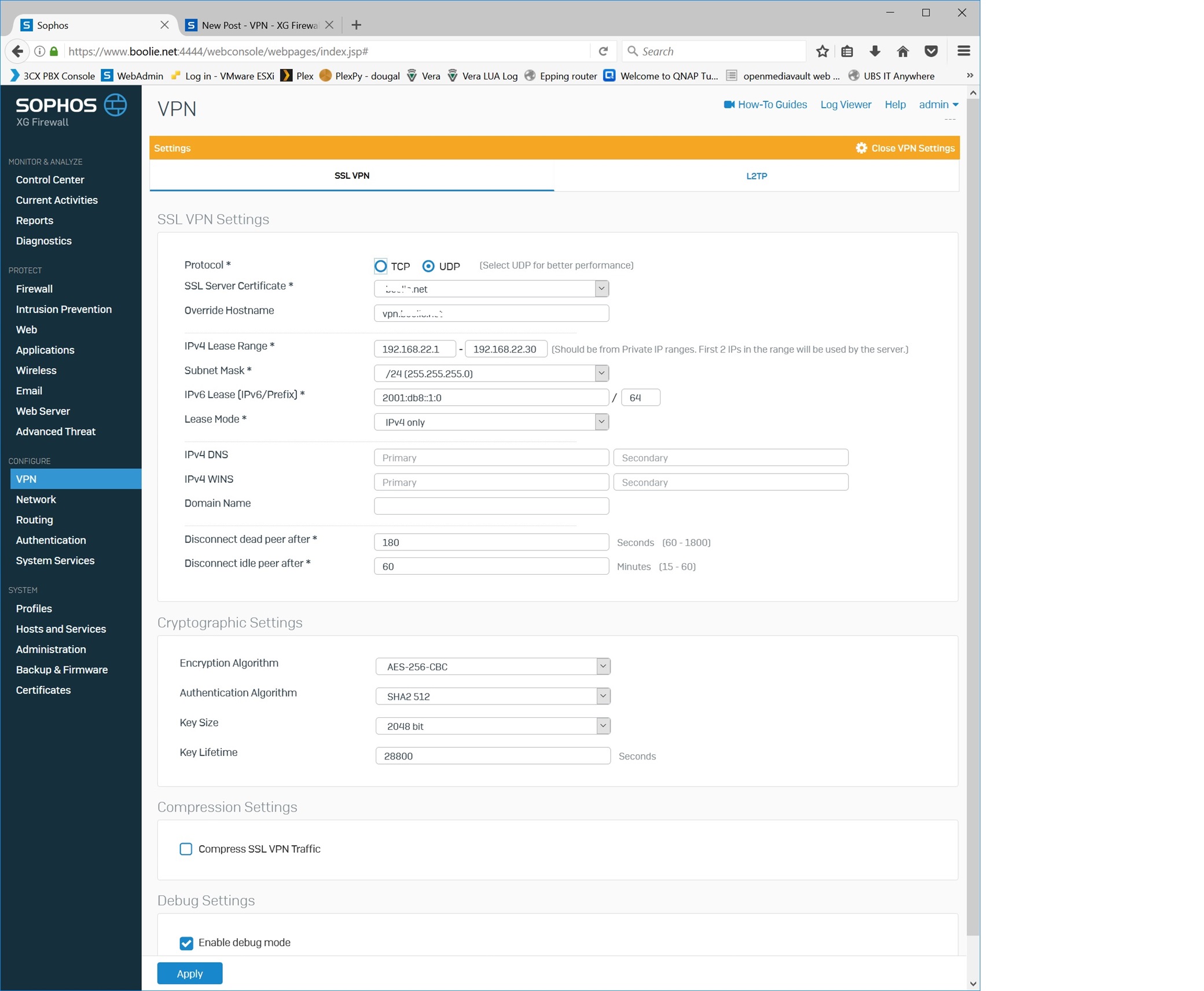
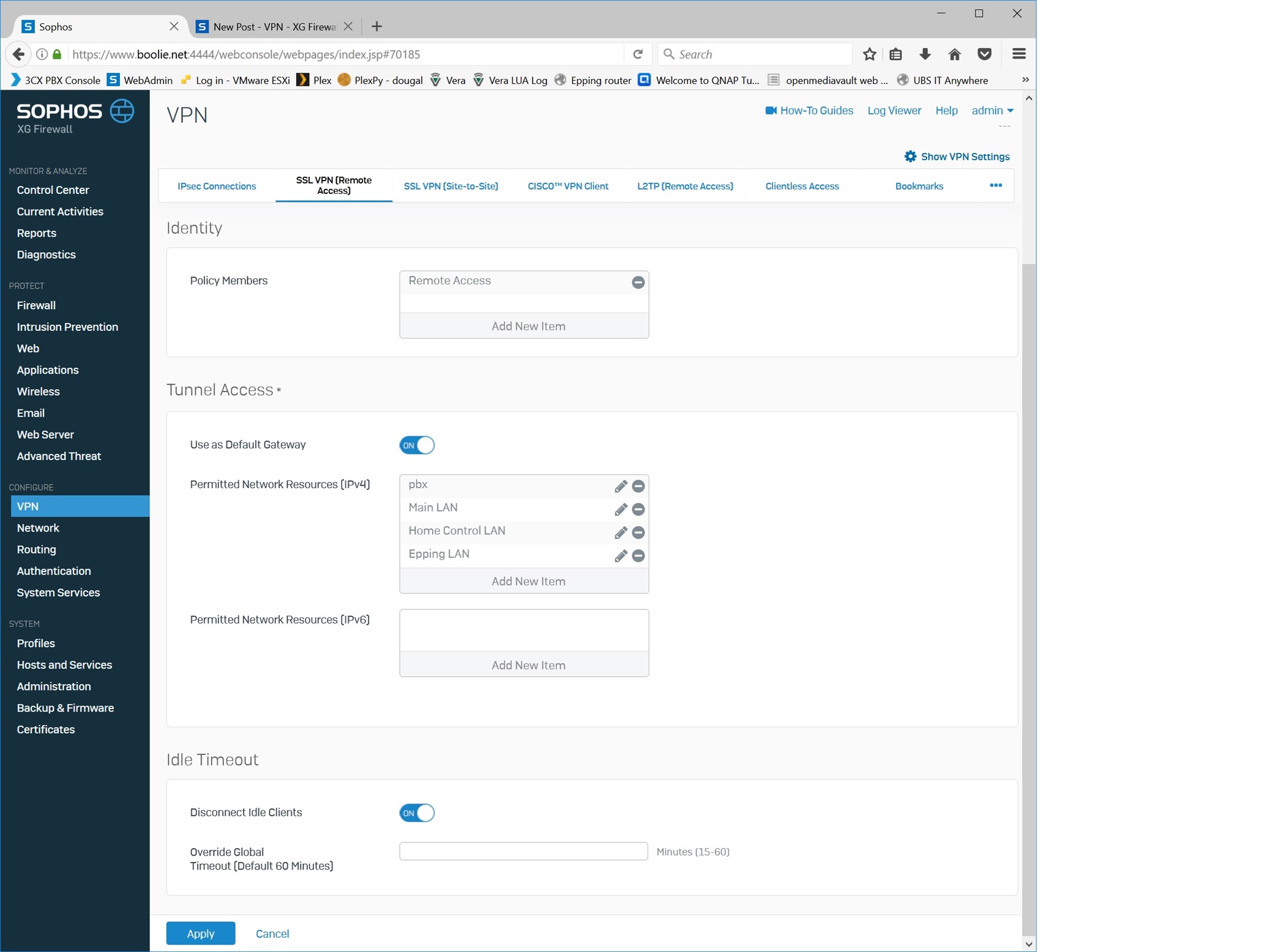
VPN config:
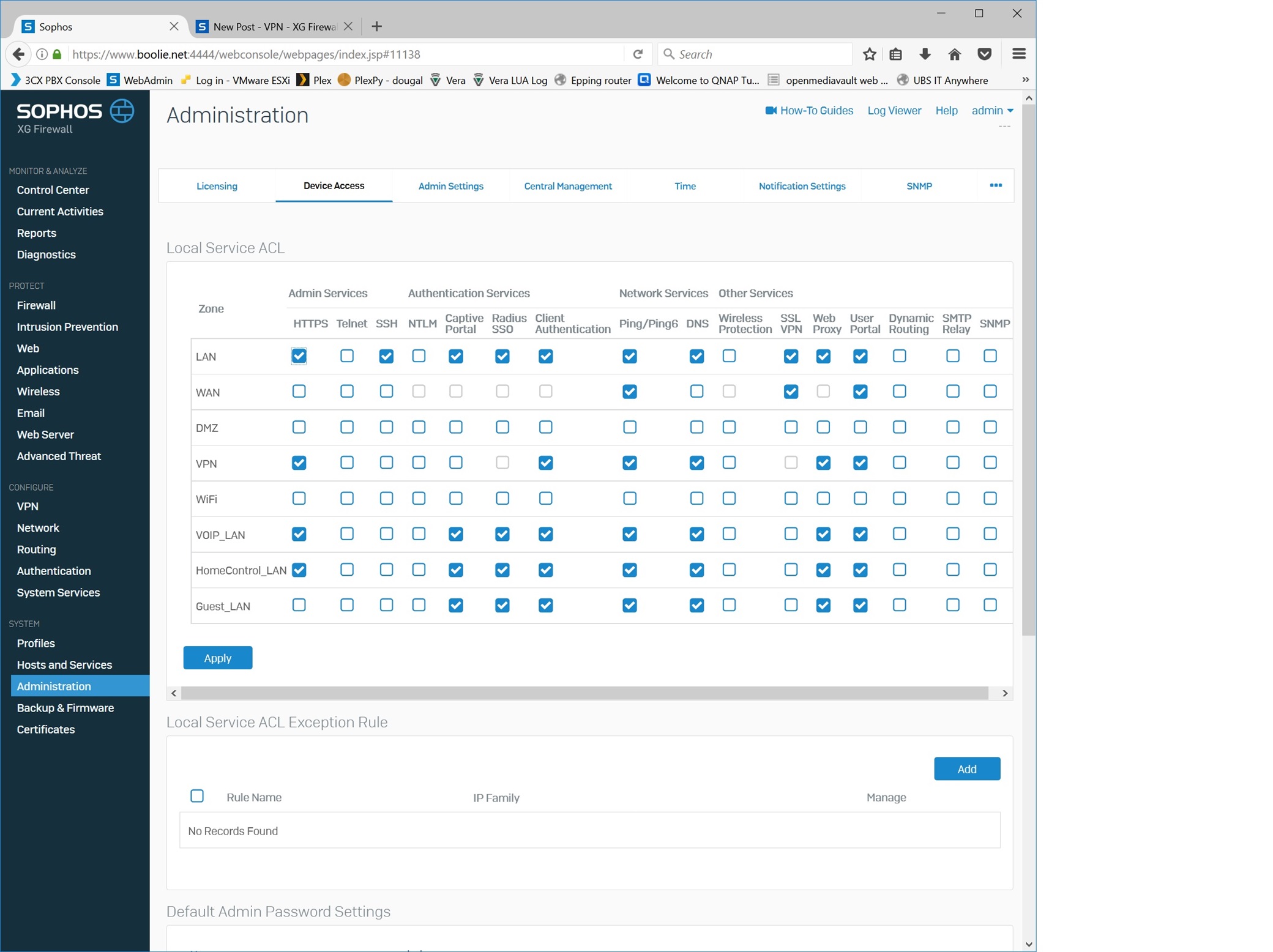
Device access:
I haven't posted the firewall rules, as I don't think we're getting that far. There is one allowing traffic from the VPN subnet to some of the LAN subnets.
Any ideas appreciated!
Thanks,
Jeff
This thread was automatically locked due to age.