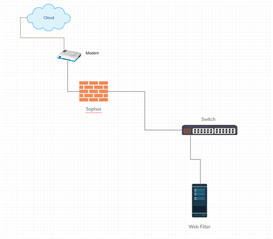
Ok so we have a client that has a barracuda 210 and they want all traffic to filter through it regardless of how it connects. I created the DHPC option and published a WPAD.dat but that is not working and barracuda is not very helpful. I was having a conversation with a senior engineer who suggested I can route traffic to it and allow only traffic from the filter out of the firewall. I'm not sure if that is possible. I was going to suggest simply putting the filter inline and physically connect the switch to the filter and the filter would connect to the firewall, but barracuda being the great product that it is has already shown to have issues after losing power. So we don't want the entire network dependent on that device.
With all that being said can I create a rule that says all outbound traffic from ip 192.168.0.20-254 go to 192.168.0.3 and all other traffic is allowed out? that way if there is an issue we can turn the rule off remotely.
This thread was automatically locked due to age.