Hello,
SFOS 16.05.2 MR-2
So I've created a firewall rule and applied web policy to to block URL category "Spyware & Malware"
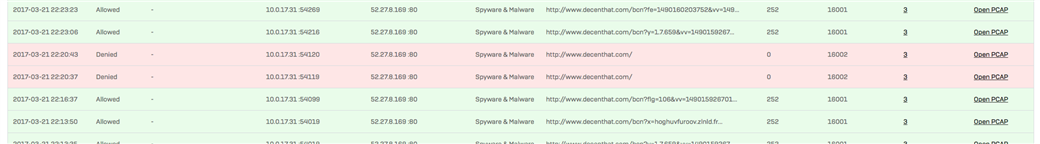
Next, I've typed a url (see screenshot, did not want to put it in plain text) and confirmed in the logs that it is blocked.
However when I visit another - permitted web site -- e.g. http://elderscrolls.wikia.com which apparently indirectly accesses that blocked web site - it is then allowed. See screenshot.
Note, same source IP, same rule.
Any ideas?
Edit1.
I've narrowed it down to the length of URL:
This is correctly blocked:
www.decenthat.com
This also is correctly blocked:
www.decenthat.com/bcn?fe=14
However adding more stuff to the request - apparently makes it allowed:
www.decenthat.com/bcn?fe=149 <---- allowed
www.decenthat.com/bcn?fe=1490168440455&vv=1490167133770 <--- also allowed
This is just silly.
This thread was automatically locked due to age.