I was having trouble getting a Authentication Policy to work with the form based login. I published a web server using Web Server Protection (WAF), pretty basic. Redirect HTTP to HTTPS and selected my SSL cert and domain name. I selected the web server, which is also HTTPS. For Protection and Intrusion Prevention, during testing, I left both blank.
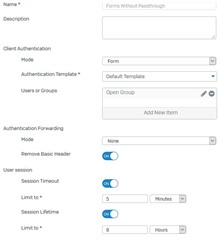
I tested access and as expected I can connect to the internal server just fine without any authentication. But this server needs to have a login from the outside world. So under Web Server -> Authentication Policies I make a basic policy called "Forms without passthrough" to simply give the users a login box without forwarding even basic authentication. In essence using the Sophos as a gate keeper for this site:
I assign the policy to the Web Server Protection rule for the server. I try to access it again and I get the standard Sophos login page. I login and it refreshes back to the login page. Try again and same thing. So I try a test user and that test user worked fine.
I then tried to hunt down the difference and the only one is my ID is part of a VPN group and the Open group while the test user is just part of the Open Group. So I tested with another user in the VPN group - it failed login again. I tested another user that's only in the open group - it worked.
So I went back into the authentication policy and added the VPN group along side the Open group. Sure enough now it works.
Is this a bug in the XG firmware? Shouldn't it check the group I specifically assigned to the policy, which all users are part of? It seems it's not doing this and I would think this is a major flaw. Maybe its checking group membership and stops at the first it finds then compares that group to the allowed ones and is failing without cycling through all groups the user is a member of? How do we get a engineer to look at this?
-Allan
This thread was automatically locked due to age.