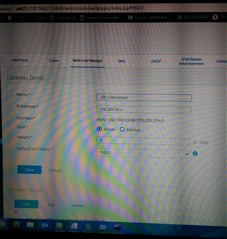
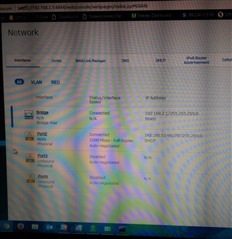
Been running into this issue with the XG series. Basically, the ISP router has the ability to go into advanced DMZ, giving the specified device the WAN address. On the SG series, this worked like a charm, the WAN link gets the public IP, internet works, and also can also still access the ISP routers admin page.
With the XG's, the firewall will get the public IP as expected, however that's where it stops. Internet doesnt come up, and cannot access the ISP routers admin page. I'm guessing it may be a manual route I need to make, however i'm not sure where i'd need to do it. If I give the WAN port an alias on the DHCP scope from the ISP modem, i'm able to get to the admin page. Any ideas?
This thread was automatically locked due to age.