Hi,
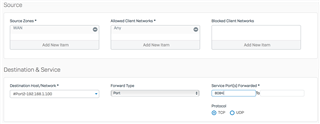
So I'm trying to setup DNAT rule to forward port 8084 from WAN interface to port 8080 on the server in LAN.
Here is the network layout: internet (public IP) -> provider modem (ports 8080-8089 redirected to 192.168.1.100) -> xg WAN(192.168.1.100) -> XG LAN(192.168.0.1) -> LAN server (192.168.0.180).
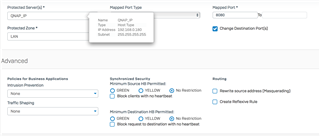
I tried different setups when it comes to firewall rule, here is an example:
Tried also with MASQ but this doesn't help.
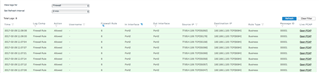
In the log viewer I can see that traffic coming to port 8084 falls under rule id 6, so the correct one, but in/out interface is the same port 2 (that is WAN interface):
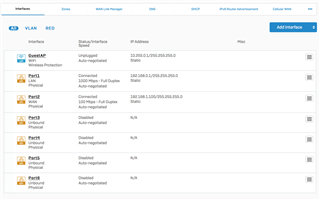
Here is the interface configuration:
Any ideas, why traffic is coming in and out the same interface, I think this is what causes issues with this setup
Thanks
This thread was automatically locked due to age.