Friends,
I am having a XG-210 UTM appliance and we now have two issues.
1. AD groups are not automatically updating in the firewall. I have imported the AD groups to firewall and the groups sync well also. We are noticing that the user's group memberships are automatically changing without our update in AD or in firewall. The restarting of authentication service in Firewall is also causing one of our marking user to get removed from his Sophos group.
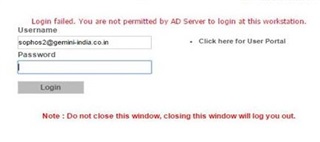
2. We noticed some of the users are removed automatically from their groups in Firewall (No change in AD groups). In our scenario we are restricting the user logins to single machines in AD level. We tried authenticating through captive portal, but it is only working for those users who have login permitted in all workstations (the login restricted users are getting a message "Login failed: you are not permitted by AD server to login this workstation"). This is same for both new and old users in the domain.
Anyone please suggest me some solution as we are in a GO-Live plan of migrating our old firewall to Sophos.
Edited Tags
[edited by: Erick Jan at 12:40 AM (GMT -7) on 16 Sep 2022]