Having quite a bit of difficulty configuring SSL VPN. I can now successfully establish an SSL VPN connection through the client (I get the green light) and confirm that I get assigned an IP from the SSL VPN pool. But I cannot connect to anything at all. When I try pinging the firewall (or any other IP address on the LAN) I get no results. When I turn on default gateway, I cannot access any external websites. It's like it's connected to nothing at all.
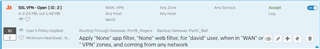
Even more odd is that the firewall rule I created shows traffic coming through:
And the logs also show traffic as being allowed:
|
2017-01-07 13:10:39
|
Firewall Rule
|
Allowed
|
david
|
2
|
tun0
|
PortB
|
10.81.234.6 :TCP(62959)
|
74.125.202.188 :TCP(5228)
|
User
|
Open PCAP
|
|
2017-01-07 13:10:06
|
Firewall Rule
|
Allowed
|
david
|
2
|
tun0
|
PortB
|
10.81.234.6 :TCP(62931)
|
75.101.136.125 :TCP(80)
|
User
|
Open PCAP
|
|
2017-01-07 13:11:06
|
Firewall Rule
|
Allowed
|
david
|
2
|
tun0
|
-
|
10.81.234.6 :TCP(62971)
|
38.112.113.153 :TCP(443)
|
User
|
Open PCAP
|
I've followed the "Configuring SSL VPN for Remote Access" guide and have checked and rechecked my settings.
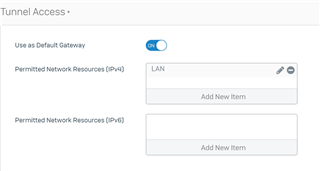
I also found another discussion that suggested a new host network be created and interface ports be deleted from the VPN config (Configure - VPN - SSL VPN (Remote Access), so I did that:
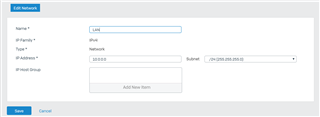
I've defined LAN as the entire subnet I'm using for the LAN:
SSL VPN settings have been left at the defaults, other than changing encryption to AES-256-CBC.
I've not bothered posting the other SSL VPN settings seeing as how I can establish the VPN connection.
This is driving me nuts. Might anyone have any suggestions as to what I might be doing wrong?
This thread was automatically locked due to age.