I have one XG430 at my data center.
I have 11 remote XG210 and 1 XG115w firewalls at remote offices.
Currently we use IPSEC/GRE tunnels and static routing to connect and route traffic between sites.
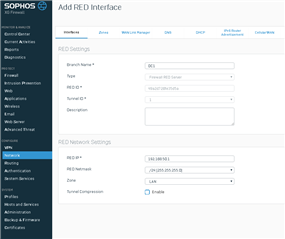
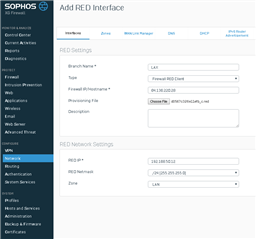
I have one site setup (remote XG115w) that uses a RED tunnel to my XG430 at my data center.
I want to change from my IPSEC/GRE tunnels to RED tunnels at all my locations.
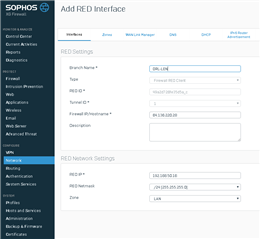
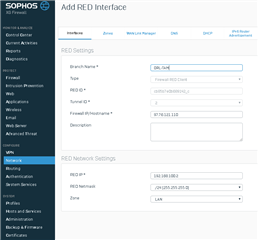
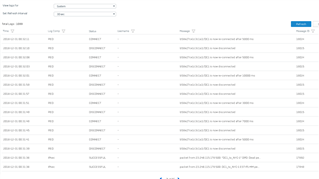
When I tried to add a second RED client (XG210 in Los Angeles) to my existing RED server (XG430 in Kansas City) at my data center, my first RED client (XG115w in Orlando) loses its connection while new client tries to connect. From the logs, it seems that the two RED clients are conflicting when they are both trying to connect.
I feel like I am missing something fundamental in all of this. I have only used XG firewalls, so I have no history with the UTM series of devices and that seems to be all the information I can find when it comes to setting up RED tunnels in a site to site setup.
Can I even do this? I was hoping I can setup multiple XG210/115 firewalls to connect back to one single XG430 firewall at data center. I thought I would be able to setup one server with many clients and just make sure the server and each client use a unique IP address in the same LAN subnet. In my case I am using 192.168.50.0/24. My RED server is 192.168.50.1 and my clients will each use a different IP address.
Can someone help explain what I am doing wrong? Is this just not how it works? Will I need to setup multiple RED servers at the data center XG430 firewall? One for each remote client? If so, does that mean I have to use a different IP address for each end of this setup like I do for my GRE tunnels (which sucks).
Thanks!
This thread was automatically locked due to age.