Dear all,
i´ve been struggling to get a Sophos XG up and running for some time. Most of the things do work now, there is only one thing i seem to be unable to solve, do you have some idea how to solve this:
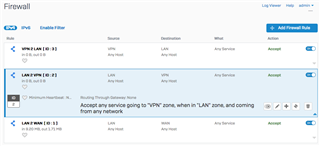
a) ipsec site 2 site vpn tunnel to some remote location defined and established
b) http / https / rdp connects to this remote locations internal network are up and running
c) as soon as i try to open a ssh connection from remote location to local one or from local one to remote, the ssh client exits with a broken pipe error
d) if i shutdown the sophos and use the old kerio appliance instead, the ssh connection works immediately
e) if i use the sophos and open a separate vpn connect on the client to the target system, the ssh connection works as well, so i suppose it might be some filtering / rewriting issue on the sophos
what i don´t understand: why is sophos inspecting / filtering the ssh vpn traffic even when the following settings are applied:
- firewall is defined without any filtering / protection
- intrusion prevention is off
- advanced threat protection & security heartbeat are off
This thread was automatically locked due to age.



