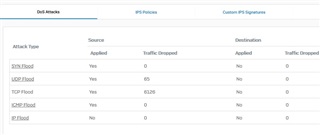
There is a sudden increase in traffic dropped under TCP Flood after upgrade to V16.01.2 (XG-135). Below screenshot for ref.
Please suggest a solution for this issue. Earlier V16 & V15 didn't used to show such huge numbers under traffic dropped.
This thread was automatically locked due to age.