This is very odd. I have HTTPS scanning disabled and have even created an exception for my IP for all HTTPS scanning. However, when going to an HTTPS site that is blocked (facebook.com for example), it is using the Sophos CA for the block page, which does not work on the endpoint, because it does not nor can have the Sophos CA installed as a trusted CA. Why does XG use the Sophos CA as the root for blocked pages if I have HTTPS inspection turned off? If I go to an HTTPS site that is NOT blocked, it works fine and it is NOT using the Sophos CA...just blocked pages are getting the "Certificate cannot be trusted" and show Sophos as the root CA in the certificate:
Here are some pictures:
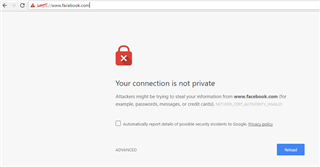
Facebook is blocked, but we are getting this instead of a blocked page:
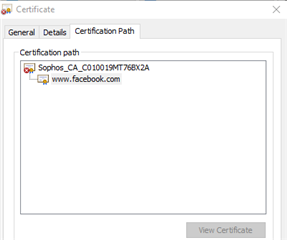
Here is the certificate...Sophos CA?!?!
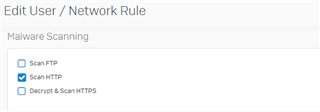
Here are my settings for HTTPS inspection:
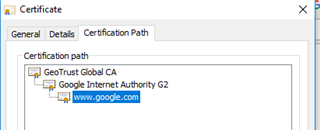
Here is an allowed HTTPS page (google) with the certificate...notice Sophos is NOT the CA:
This thread was automatically locked due to age.