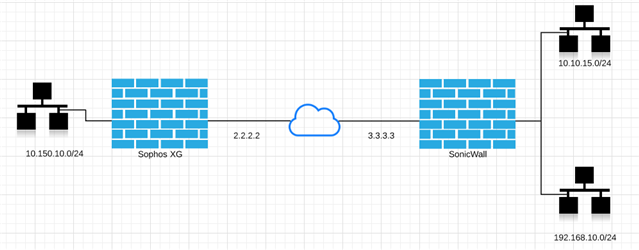
Good afternoon,
I am on the latest release of Xg 16 and seem to be having an ongoing issue with IPSEC VPN tunnels where there are multiple networks on the remote end.
It seems that a route is only created for one of the networks and not the others. It seems to be random which remote network the route gets created for. As such the network without the route doesn't work via the VPN.
Is anyone else experiencing this issue?
Thank you.
Alex
This thread was automatically locked due to age.