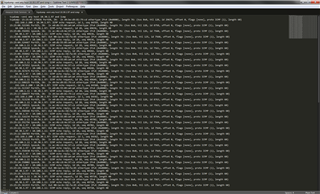
We recently setup site to site tunnels from our new XG230 running 16.01.1 to another XG, Cisco ASA and AWS. All are working fine except the AWS tunnel will drop pings intermittently from the 2 LAN's behind the XG to the servers in the AWS VPC. I used the generic VPN configuration AWS provides. pcap shows no gateway on incoming response.
|
2016-10-19 15:00:07
|
PortE5
|
ipsec0
|
IPv4
|
10.100.1.11
|
10.30.1.97
|
ICMP
|
--
|
3
|
Forwarded
|
512
|
|
|
2016-10-19 15:00:07
|
PortE5
|
IPv4
|
10.100.1.11
|
10.30.1.97
|
ICMP
|
--
|
0
|
Incoming
|
No Gateway
|
This thread was automatically locked due to age.