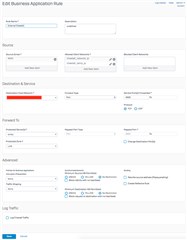
I'm trying to build a business rule for incoming traffic from an fqdn resolved host. As you can see in the image, I have a rule that allows network traffic from two objects. One is an IP address object and the other is an FQDN host that resolves to the exact same IP when I hover over it or issue a DHCP lookup. However, if I set this rule with only the FQDN object in place on the Allowed Client Networks section, traffic is blocked from the host. If I make the rule to include the IP address object in the Allowed Client Network section, it works perfectly (obviously I can leave the FQDN object off completely in this case and it still works).
Is there something I'm missing? This type of rule worked perfectly under my UTM 9 setup using an FQDN.
This thread was automatically locked due to age.