I am trying to get a RED Site to Site connection between a UTM (server) and an XG (client) to work. Here is what I have done so far:
1. RED Zone
I defined a RED zone with similar characteristics to the LAN zone.
2. RED Interface in XG
Defined RED interface, provided provisioning file from UTM and assigned zone as RED. Works like a charm!
3. Firewall Rule
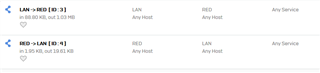
Added two simple zone rules. RED to LAN and LAN to RED.
4. Static Routing
This is where I am struggling. In the UTM we defined our rule as gateway under static routing, but I can't seem to find the same in XG. I am guessing that I need to setup a Unicast Route with the desired network on the UTM as the destination and the interface pointing to the RED interface defined above. But what is the gateway? On the UTM the gateway IP points to an interface, but how does this work on the XG?
Thank you for your feedback!
Cheers,
Jens
This thread was automatically locked due to age.