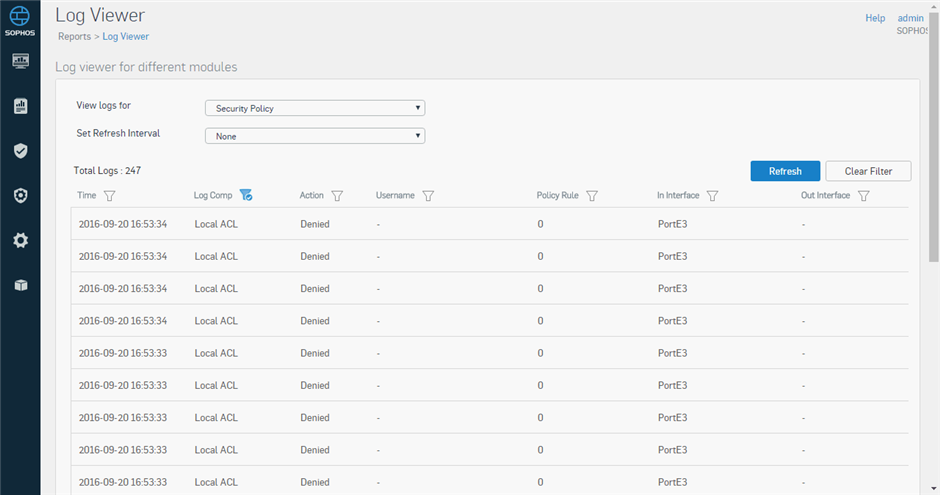
Dear Sir,
In my XG firewall, I see a lot of Local ACL/Invalid Traffic log.
With the "drop-packet-capture" function in console mode, I got the following log.
2016-09-20 16:54:06 0103021 IP 10.1.30.37.137 > 10.1.255.255.137 : proto UDP: packet len: 58 checksum : 60294
0x0000: 4500 004e 4de0 0000 8011 ba98 0a01 1e25 E..NM..........%
0x0010: 0a01 ffff 0089 0089 003a eb86 8c49 0110 .........:...I..
0x0020: 0001 0000 0000 0000 2045 4446 4145 4445 .........EDFAEDE
0x0030: 4c45 4e44 4144 4243 4143 4143 4143 4143 LENDADBCACACACAC
0x0040: 4143 4143 4143 4141 4100 0020 0001 ACACACAAA.....
Date=2016-09-20 Time=16:54:06 log_id=0103021 log_type=Firewall log_component=Local_ACLs log_subtype=Denied log_status=N/A log_priority=Alert duration=N/A in_dev=PortE3 out_dev= inzone_id=1 outzone_id=4 source_mac=00:0c:29:b7:41:d3 dest_mac=ff:ff:ff:ff:ff:ff l3_protocol=IP source_ip=10.1.30.37 dest_ip=10.1.255.255 l4_protocol=UDP source_port=137 dest_port=137 fw_rule_id=0 policytype=0 live_userid=0 userid=0 user_gp=0 ips_id=0 sslvpn_id=0 web_filter_id=0 hotspot_id=0 icap_id=0 app_filter_id=0 app_category_id=0 app_id=0 category_id=0 bandwidth_id=0 up_classid=3689628094131339264 dn_classid=0 source_nat_id=0 cluster_node=0 inmark=0 nfqueue=0 scanflags=0 gateway_offset=0 max_session_bytes=0 drop_fix=0 ctflags=0 connid=0 masterid=2475419264 status=0 state=256 sent_pkts=N/A recv_pkts=N/A sent_bytes=N/A recv_bytes=N/A tran_src_ip=N/A tran_src_port=N/A tran_dst_ip=N/A tran_dst_port=N/A
I create a rule to drop the udp 137~139 broadcast package and move to top.
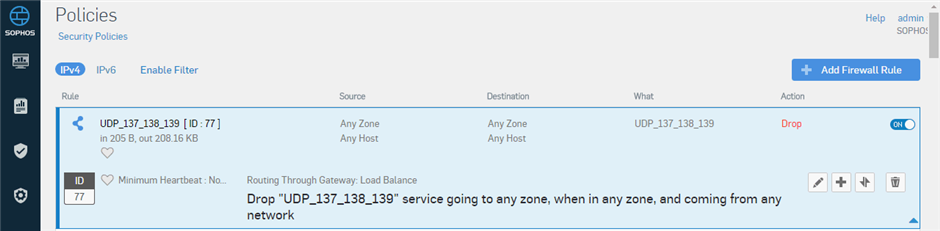
But it don't work, the log viewer still the Local ACL/Invalid Traffic log...
How should I do to hidden the lots of udp 137 log?
Shunze
This thread was automatically locked due to age.