Hi there,
right now I am really happy with my Sophos XG firewall - although I am still trying to work out a problem with my AP15 (thanks for your support sachin :-)
There is only one other matter I would like to know how to solve:
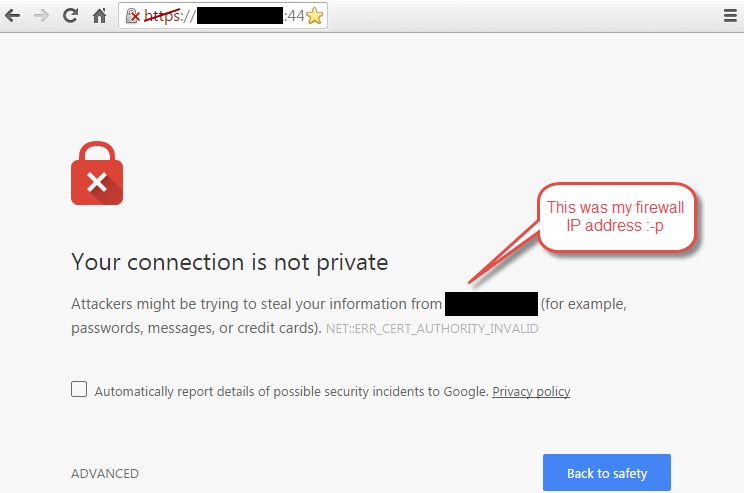
I am using Chrome on Windows and whenever I want to access the web interface / login following message appears:
Now I am going for ADVANCED and choose Proceed to XXX.XXX.XXX.XXX (IP-address-of-my-firewall).
Problem is that whenever I clear my Chrome history and cache I will have to do this all over again and the red line over https in the address bar is also not my favorite :-p
I also already tried to install the Sophos SSL certificate.
Anyone an idea how to solve this permanently without using HTTP instead of HTTPS?
Maybe someone knows how to install the certificate so that this message will disappear (working for Chrome - might I remind you) :-)
This thread was automatically locked due to age.