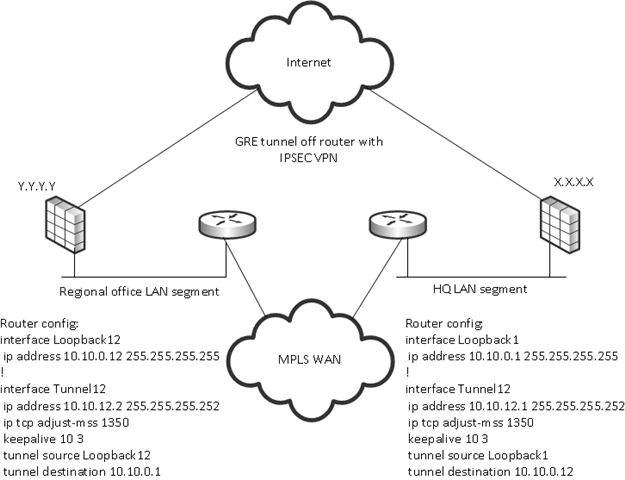
Background, trying to move from Cisco ASAs to XG platform. We presently route a GRE tunnel over IPSec connection between our regional offices and HQ as shown in this screenshot.
Am working on regional office XG with HQ being ASA. Can't get host-to-host VPN to come online. Have also tried site-to-site without much success. Would appreciate some input from the community.
ASA config at HQ
crypto map Outside_map 1 match address Outside_cryptomap_2
crypto map Outside_map 1 set peer Y.Y.Y.Y
crypto map Outside_map 1 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map Outside_map 1 set ikev2 ipsec-proposal AES192 AES256
group-policy GroupPolicy_Y.Y.Y.Y internal
group-policy GroupPolicy_Y.Y.Y.Y attributes
vpn-tunnel-protocol ikev1 ikev2
tunnel-group Y.Y.Y.Y type ipsec-l2l
tunnel-group Y.Y.Y.Y general-attributes
default-group-policy GroupPolicy_Y.Y.Y.Y
tunnel-group Y.Y.Y.Y ipsec-attributes
ikev1 pre-shared-key *****
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
access-list Outside_cryptomap_2 extended permit ip object-group Loopback-HQ object-group Loopback-REG
object-group network Loopback-HQ
network-object host 10.10.0.1
object-group network Loopback-REG
network-object host 10.10.0.12
Sophos configs
And info from the command line
console> show vpn connection status
interface lo/lo ::1
interface Port2/Port2 Y.Y.Y.Y
interface Port2/Port2 Y.Y.Y.Y
%myid = (none)
debug none
algorithm ESP encrypt: id=2, name=ESP_DES, ivlen=8, keysizemin=64, keysizemax=64
algorithm ESP encrypt: id=3, name=ESP_3DES, ivlen=8, keysizemin=192, keysizemax=192
algorithm ESP encrypt: id=6, name=ESP_CAST, ivlen=8, keysizemin=40, keysizemax=128
algorithm ESP encrypt: id=7, name=ESP_BLOWFISH, ivlen=8, keysizemin=40, keysizemax=448
algorithm ESP encrypt: id=11, name=ESP_NULL, ivlen=0, keysizemin=0, keysizemax=0
algorithm ESP encrypt: id=12, name=ESP_AES, ivlen=8, keysizemin=128, keysizemax=256
algorithm ESP encrypt: id=13, name=(null), ivlen=8, keysizemin=160, keysizemax=288
algorithm ESP encrypt: id=252, name=ESP_SERPENT, ivlen=8, keysizemin=128, keysizemax=256
algorithm ESP encrypt: id=253, name=ESP_TWOFISH, ivlen=8, keysizemin=128, keysizemax=256
algorithm ESP auth attr: id=1, name=AUTH_ALGORITHM_HMAC_MD5, keysizemin=128, keysizemax=128
algorithm ESP auth attr: id=2, name=AUTH_ALGORITHM_HMAC_SHA1, keysizemin=160, keysizemax=160
algorithm ESP auth attr: id=5, name=AUTH_ALGORITHM_HMAC_SHA2_256, keysizemin=256, keysizemax=256
algorithm ESP auth attr: id=6, name=AUTH_ALGORITHM_HMAC_SHA2_384, keysizemin=384, keysizemax=384
algorithm ESP auth attr: id=7, name=AUTH_ALGORITHM_HMAC_SHA2_512, keysizemin=512, keysizemax=512
algorithm ESP auth attr: id=251, name=(null), keysizemin=0, keysizemax=0
algorithm IKE encrypt: id=1, name=OAKLEY_DES_CBC, blocksize=8, keydeflen=64
algorithm IKE encrypt: id=3, name=OAKLEY_BLOWFISH_CBC, blocksize=8, keydeflen=128
algorithm IKE encrypt: id=5, name=OAKLEY_3DES_CBC, blocksize=8, keydeflen=192
algorithm IKE encrypt: id=7, name=OAKLEY_AES_CBC, blocksize=16, keydeflen=128
algorithm IKE encrypt: id=65004, name=OAKLEY_SERPENT_CBC, blocksize=16, keydeflen=128
algorithm IKE encrypt: id=65005, name=OAKLEY_TWOFISH_CBC, blocksize=16, keydeflen=128
algorithm IKE encrypt: id=65289, name=OAKLEY_TWOFISH_CBC_SSH, blocksize=16, keydeflen=128
algorithm IKE hash: id=1, name=OAKLEY_MD5, hashsize=16
algorithm IKE hash: id=2, name=OAKLEY_SHA1, hashsize=20
algorithm IKE hash: id=4, name=OAKLEY_SHA2_256, hashsize=32
algorithm IKE dh group: id=1, name=OAKLEY_GROUP_MODP768, bits=768
algorithm IKE dh group: id=2, name=OAKLEY_GROUP_MODP1024, bits=1024
algorithm IKE dh group: id=5, name=OAKLEY_GROUP_MODP1536, bits=1536
algorithm IKE dh group: id=14, name=OAKLEY_GROUP_MODP2048, bits=2048
algorithm IKE dh group: id=15, name=OAKLEY_GROUP_MODP3072, bits=3072
algorithm IKE dh group: id=16, name=OAKLEY_GROUP_MODP4096, bits=4096
algorithm IKE dh group: id=17, name=OAKLEY_GROUP_MODP6144, bits=6144
algorithm IKE dh group: id=18, name=OAKLEY_GROUP_MODP8192, bits=8192
stats db_ops.c: {curr_cnt, total_cnt, maxsz} :context={0,1,64} trans={0,1,1296} attrs={0,1,432}
"VPN_to_HQ": Y.Y.Y.Y[10.10.0.12]---Y.Y.Y.Z...%virtual[10.10.0.1]===?; unrouted; eroute owner: #0
"VPN_to_HQ": srcip=unset; dstip=unset;
"VPN_to_HQ": ike_life: 28800s; ipsec_life: 3600s; rekey_margin: 360s; rekey_fuzz: 100%; keyingtries: 0
"VPN_to_HQ": policy: PSK+ENCRYPT+COMPRESS+TUNNEL+PFS+failureDROP; prio: 32,32; interface: Port2; encap: esp;
"VPN_to_HQ": dpd: action:restart; delay:30; timeout:120;
"VPN_to_HQ": newest ISAKMP SA: #0; newest IPsec SA: #0;
"VPN_to_HQ": IKE algorithms wanted: AES_CBC(7)_128-MD5(1)-MODP1024(2), AES_CBC(7)_128-SHA1(2)-MODP1024(2), 3DES_CBC(5)_000-MD5(1)-MODP1024(2); flags=strict
"VPN_to_HQ": IKE algorithms found: AES_CBC(7)_128-MD5(1)_128-MODP1024(2), AES_CBC(7)_128-SHA1(2)_160-MODP1024(2), 3DES_CBC(5)_192-MD5(1)_128-MODP1024(2)
"VPN_to_HQ": ESP algorithms wanted: AES(12)_128-MD5(1), AES(12)_128-SHA1(2), 3DES(3)_000-MD5(1); flags=strict
"VPN_to_HQ": ESP algorithms loaded: AES(12)_128-MD5(1), AES(12)_128-SHA1(2), 3DES(3)_000-MD5(1); flags=strict
console>
console> show vpn IPSec-logs
Jun 27 15:37:52 "VPN_to_HQ"[115] X.X.X.X #118: ignoring informational payload, type INVALID_COOKIE
Jun 27 15:37:52 "VPN_to_HQ"[115] X.X.X.X #118: received and ignored informational message
Jun 27 15:37:55 packet from X.X.X.X:500: next payload type of ISAKMP Message has an unknown value: 33
Jun 27 15:37:55 packet from X.X.X.X:500: sending notification INVALID_MAJOR_VERSION to X.X.X.X:500
Jun 27 15:38:02 packet from X.X.X.X:500: next payload type of ISAKMP Message has an unknown value: 33
Jun 27 15:38:02 packet from X.X.X.X:500: sending notification INVALID_MAJOR_VERSION to X.X.X.X:500
Jun 27 15:38:17 packet from X.X.X.X:500: next payload type of ISAKMP Message has an unknown value: 33
Jun 27 15:38:17 packet from X.X.X.X:500: sending notification INVALID_MAJOR_VERSION to X.X.X.X:500
Jun 27 15:38:32 "VPN_to_HQ"[115] X.X.X.X #118: max number of retransmissions (2) reached STATE_MAIN_R2
Jun 27 15:38:32 "VPN_to_HQ"[115] X.X.X.X: deleting connection "VPN_to_HQ" instance with peer X.X.X.X {isakmp=#0/ipsec=#0}
Jun 27 15:38:46 packet from X.X.X.X:500: next payload type of ISAKMP Message has an unknown value: 33
Jun 27 15:38:46 packet from X.X.X.X:500: sending notification INVALID_MAJOR_VERSION to X.X.X.X:500
I added a static route for 10.10.0.1 to point to the outside interface gateway and that didn't seem to matter either.
This thread was automatically locked due to age.