I have installed an Aruba RAP109 supplied by work to provide a permanent VPN to the office. The setup works well on the UTM 9.4xx, but the link is the congested one. So I tried again to to move it to the XG which has a faster less congested link. Failed at initial setup.
This time though I setup up a policy to allow the RAP out on UDP port 4500. XG reports the policy is not used. The RAP can access the controller at work, but as soon as I apply a load the connection drops.
I have tried a number of different policy settings with a range from total failure to short term success.
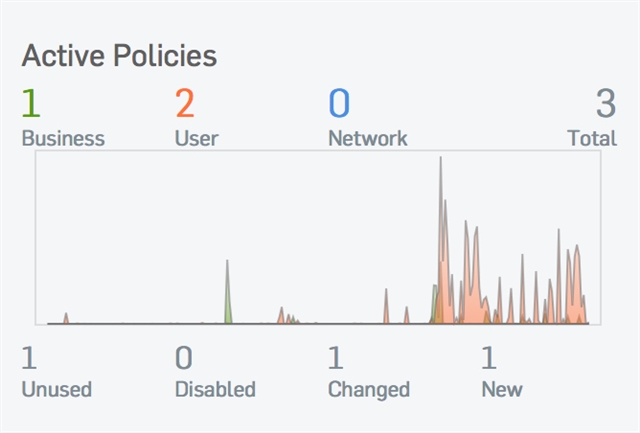
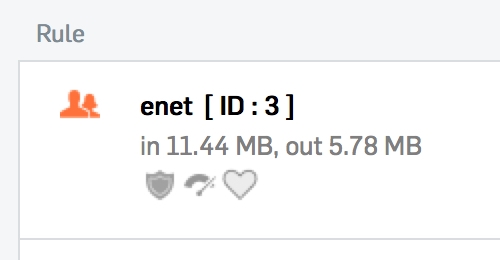
All the time the XG shows this policy as being ignored. The policy show traffic through it in both directions. When I examine the current activity report, this report shows traffic through the rule even though the XG dashboard still shows it as being ignored.
I changed the policy settings to allow all traffic on all ports out, still showing in the activity report as rule 3. A connection occurs until loaded then drops. After many hours of testing and waiting, 5 minutes for the RAP to reset and a similar time for the XG to settle down, I gave up and moved the RAP back to the UTM 9.4 where it immediately connected and stays connected.
The XG shows packets outgoing, but nothing returning most of the time, except when the RAP connects for a short connection.
I have tried with and without web and application rules. I have tried specific IP address and then the clientless group. I have tried specific port that I know the RAP uses and reports on in the XG, then no port limitation. I have tried with and without MASQ.
Something drastically wrong with this product that requires so much effort and still does not work.
This thread was automatically locked due to age.