Hello,
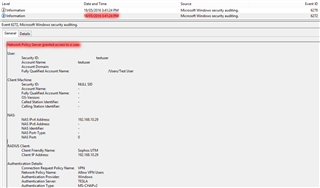
I am having an issue where VPN authentication is failing for all users when using radius as the authentication method. Local user authentication is working as long as the user in the user directory has not been created from Active Directory.
The radius server is granting access to the user authentication request, but the XG logs are denying the connection. This occurs for MS_CHAPv2 or PAP authentication requests.
I have tried with both console commands set vpn l2tp authentication MS_CHAPv2 and set vpn l2tp authentication ANY.
Any suggestions are much appreciated.
Thankyou,
Derek
This thread was automatically locked due to age.