Hi,
I am really desperate with my new Sophos XG 85 and seeking your advice. I have successfully setup SSL VPN (Remote Access) on my Sophos XG 85 and users can connect and reach the internal LAN and internet. But as mentioned in the subject users are experiencing terrible latency issues and ping times are the worst I have ever seen ranging from 70ms to > 1000ms with an average round-trip from 450 ms. It doesn't matter if I am connected via LAN, WIFI or mobile 4G LTE or if I ping a LAN address like 192.168.100.1 or www.sophos.com. I tried different clients and connected from Windows, Mac OS X and Android. It doesn't make a difference.
My setup is as follows:
[ Internet ] --- [ Router (192.168.2.1) ] --- [ Sophos Port2 (192.168.2.2) ] --- [ Sophos Port1 (192.168.100.1) ] --- [Switch ] --- [ LAN (192.168.100.0/24) ]
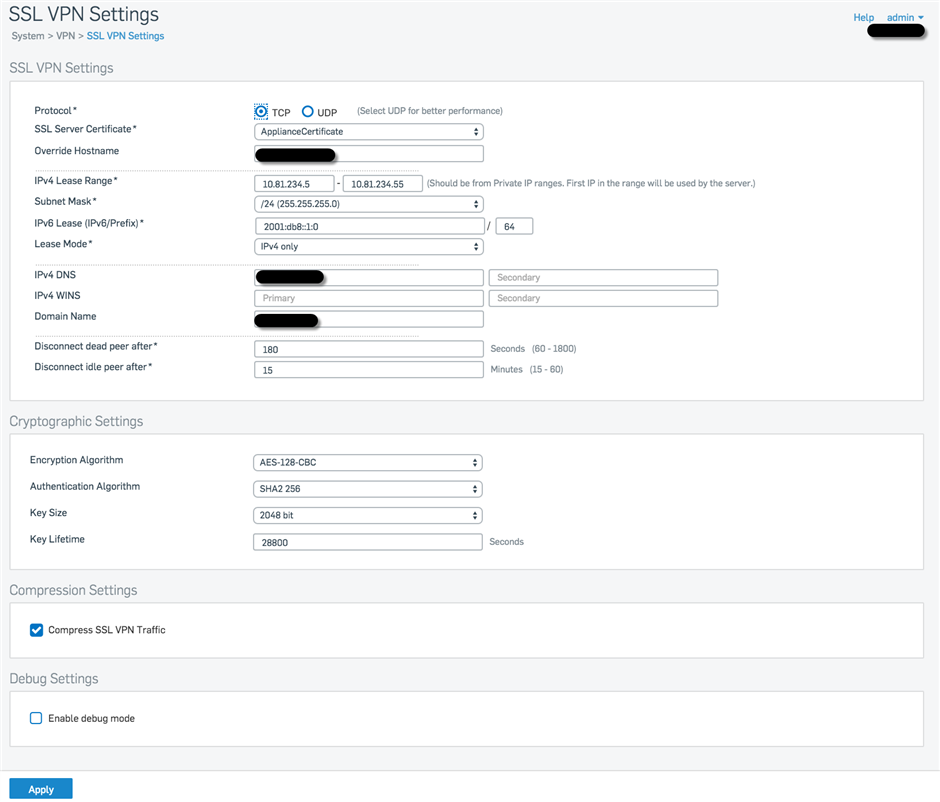
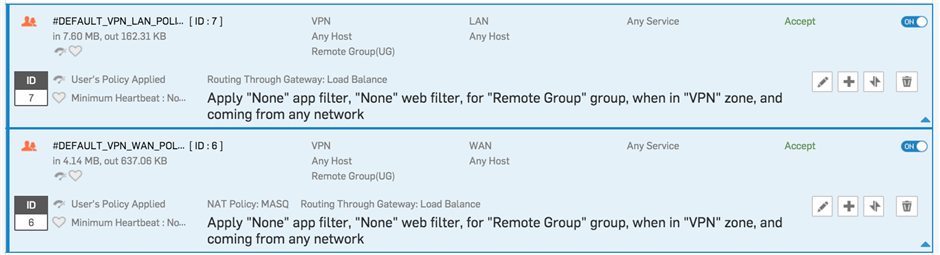
The [ Router ] is forwarding port 8443 to [ Sophos Port2 (192.168.2.2) ] . Enclosed you can find my SSL VPN Setting and the policy I have set up.
Any help is really appreciated.
Regards
Ingo
This thread was automatically locked due to age.