Hi everyone,
I'm trying to create a VLAN for some Ubiquiti UniFi access points and I just can't seem to get it working correctly.
In my interface for the access points I assigned them a VLAN ID of 2, as shown here: http://screencast.com/t/s8VuPEud7
In my Cisco SG-500 switch I created a VLAN as shown here: http://screencast.com/t/wcAMNUwJ
I set all the ports to Trunk and accept all frames as shown here: http://screencast.com/t/TO0EcTH6iY
Since the AP that is plugged into the port of the switch will be passing frames with the default VLAN of 1, and also a VLAN of 2. I left the port untagged for the VLAN 1 as shown here http://screencast.com/t/fjVBw9gcal and then the VLAN ID 2 is tagged on the port the AP is connected to as well as the port to the machine running Sophos XG is connected to, as shown here: http://screencast.com/t/MdJhozsoI
Here you can see those ports and the VLAN memberships: http://screencast.com/t/b9P8sWJ1m
In Sophos I then created a new Zone for the guests as shown here: http://screencast.com/t/IRTPRWYrsG
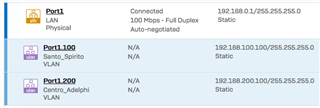
I then created a new VLAN interface and assigned it an ID of 2, then assigned it to the zone I created in the previous step, as shown here: http://screencast.com/t/tA77JnCRdFDt
Finally, I created a DHCP service and selected the VLAN interface that I created from the previous step, as shown here: http://screencast.com/t/IA5yZnYtwP
I thought that's all I needed, but it doesn't appear to be working. My devices are unable to obtain an IP address when the connect to the AP. I'm sure I've missed a step or did something incorrectly. Any assistance would be greatly appreciated.
Thanks,
Christopher
This thread was automatically locked due to age.