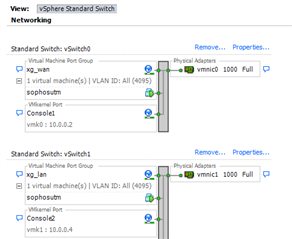
I am looking interpose two physical interfaces in the XG (VM on ESXi 6) on a trunk link between an edge router and L3 core switch, the aim being to apply policy/ monitor the various VLANs passing through the trunk without having the XG routing anything - Think VirtualWire on a Palo Alto.
It seems this isn't possible? Firstly, VLANs have to be assigned L3 IPs and secondly, physical interfaces forming part of a bridge cannot be further divided into sub-interfaces.
Would you be able to confirm please?
This thread was automatically locked due to age.