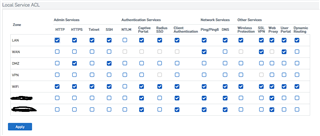
Creating an additional VLAN and Zones, where I did not give access to Admin services, allows users from this vlan to access the https://xglanip:4444 interface (because a Policy rule from lan to add. zone exist with all services).
This is not save. See screenshot.
This thread was automatically locked due to age.