Hello.
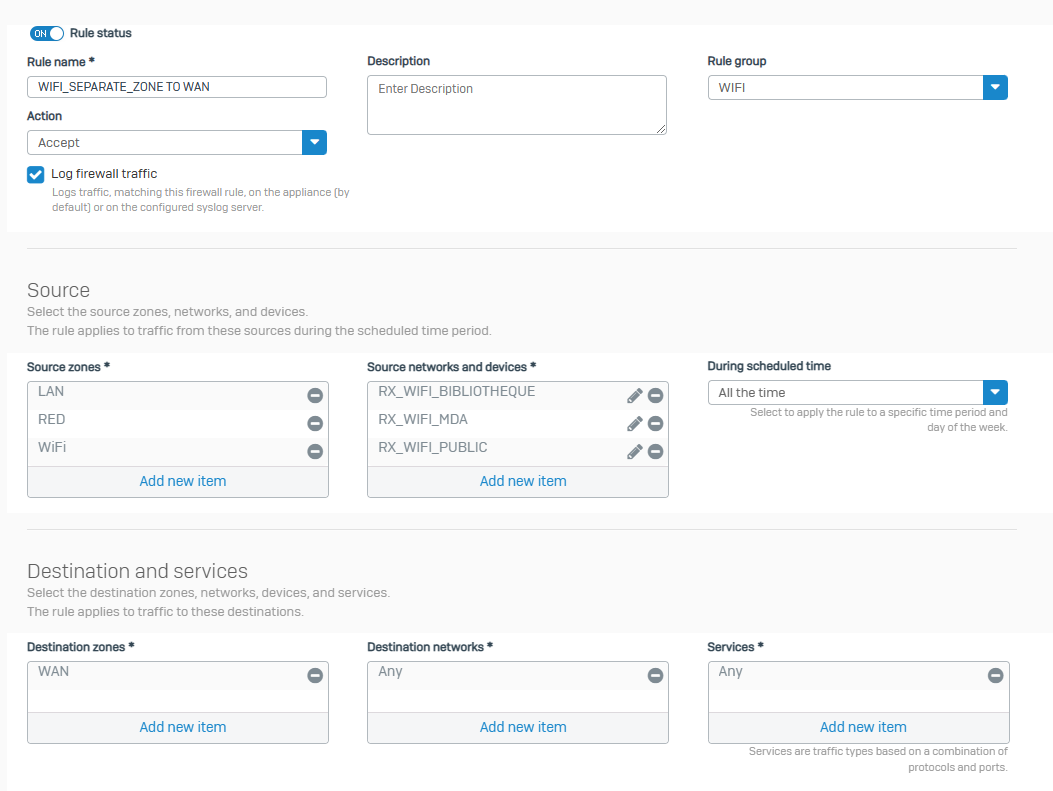
I have created 1 wifi network bridge to lan and 3 wifi networks on separate zone.
All wifi networks operate just fine for as long as my APX320 are connected on the LAN of the XGS2300.
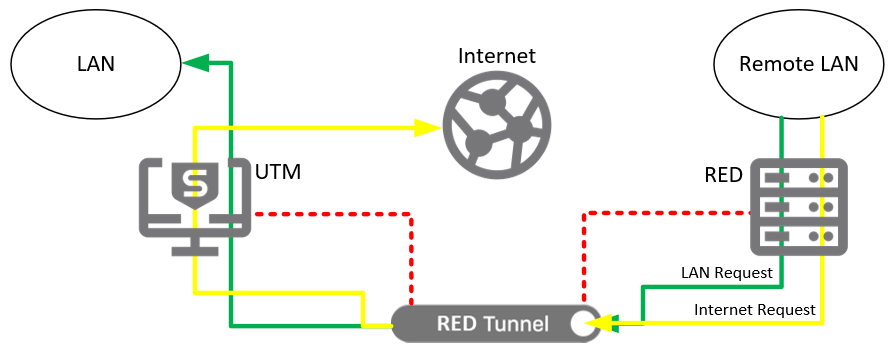
On my RED 60 i can access the internet through my bridged to lan wifi network but not through my other separate zone wifi networks.
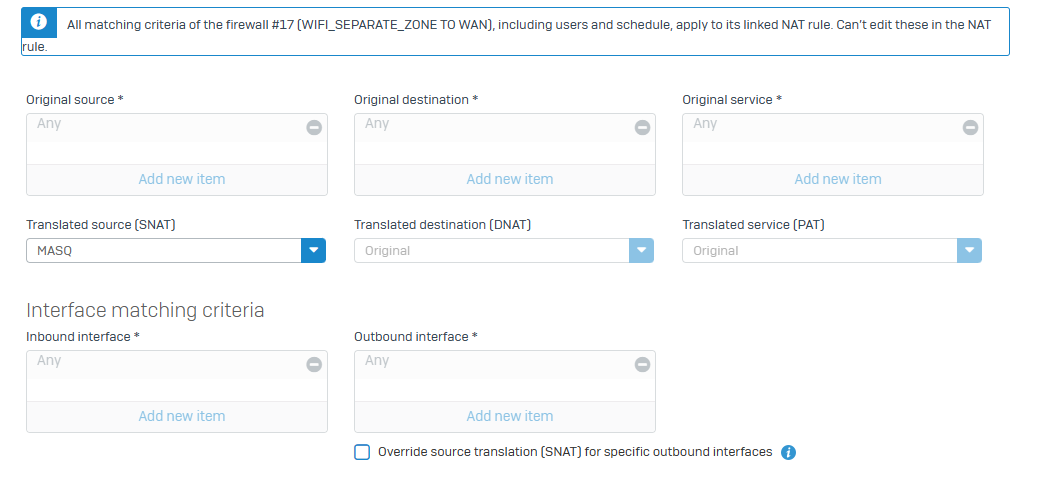
I went through rules and policies in order to enable as follows but it doesnt work :
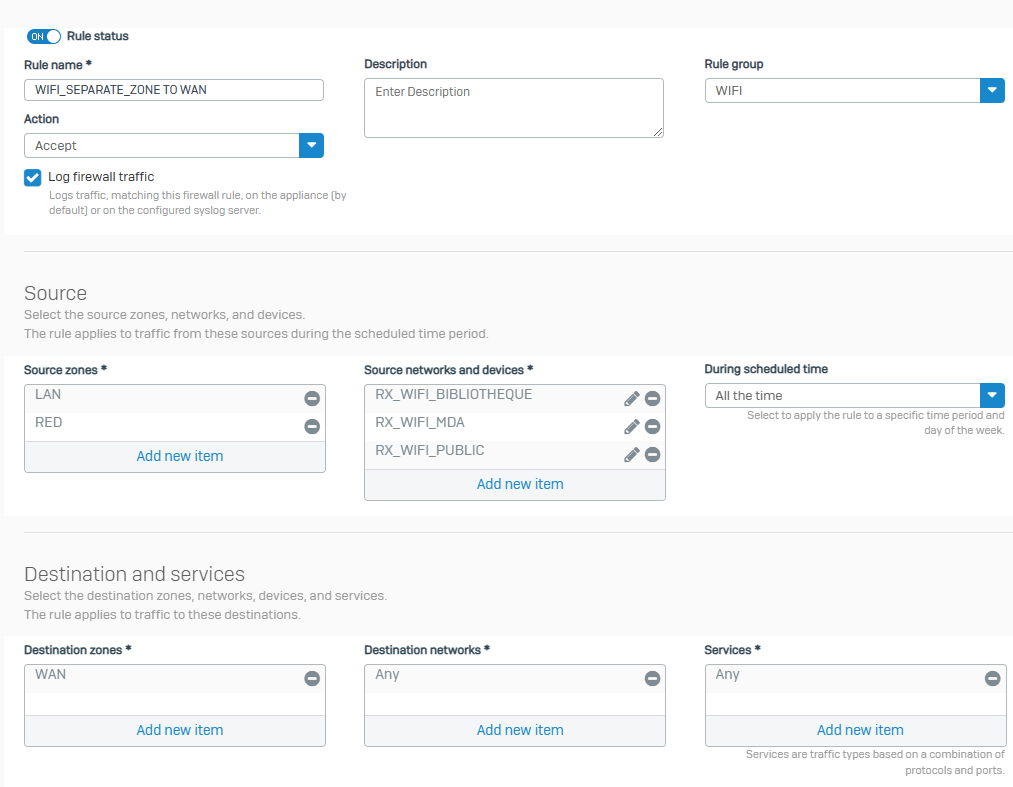
Would you give me an hint on why it is not working ?
Wireless protection is enabled.
DHCP and DNS dont seem to be the problem since the connections work while connected to the XGS.
I am missing something related to the RED.
Also, i can ping google name or 8.8.8.8 but cant access through an browser
Best regards,
JF
This thread was automatically locked due to age.