Hi there,
is this a possible valid portscan for the XGS 2100?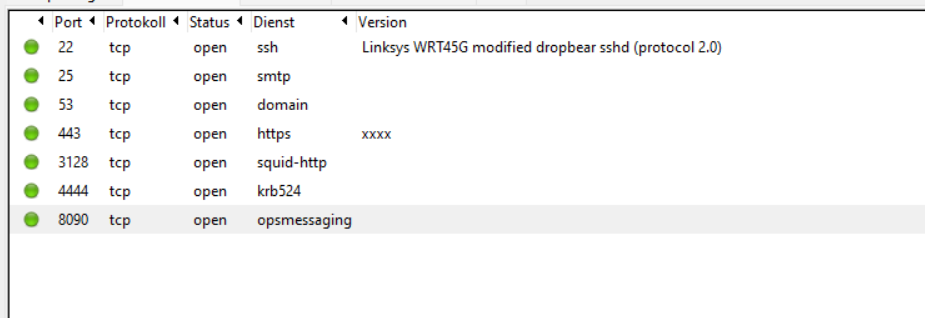
I'm wondering about the Linksys WRT56G modified dropbear sshd Port.
Thanks!
Best Regards
This thread was automatically locked due to age.
Hi there,
is this a possible valid portscan for the XGS 2100?
I'm wondering about the Linksys WRT56G modified dropbear sshd Port.
Thanks!
Best Regards
Hi Dennis Wauer Thank you for reaching out to the Sophos community team. Can you please help us with the below details to narrow down the situation?
How this Port scan was performed? From Outside or from the LAN segment?
On which IP this Port scan was performed? The IP on which this port scan was performed is directly assigned and configured on XGS? if it is directly assigned and configured on XGS then is it WAN IP?
Is there any DNAT/Port forwarding configured for any in-house device to map the above services or any of the services listed in the above port scan result?
If this has been scanned from the WAN side, Does XG WAN has private IP over WAN on which requests are landing from the next hop router via port forwarding on it?
Regards,
Vishal Ranpariya
Technical Account Manager | Sophos Technical Support
Sophos Support Videos | Knowledge Base | @SophosSupport | Sign up for SMS Alerts |
If a post solves your question use the 'This helped me' link.
Hi Vishal,
thanks for your fast reply on my topic.
The scan was performaned using Zenmap on Microsoft Windows 11 from inside the LAN, with the following command:
nmap -sS -sU -T4 -A -v 10.0.1.1
Yes, the IP-Address where with port scan was performed is directly assigned to the Sophos XGS. We are using for WAN the Sophos DSL Module. (=> Screenshot 1)
No there is no DNAT / Port forwarding configured for any of these services.
We have a dynamic public IP-Address assigned for the WAN, which get assigned by the DSL Module.
Regards,
Dennis
Hi Dennis Wauer Can you please capture tcpdump and PCAP on XG on ssh service port 22 when you perform scanning to confirm who is replying or how the 22 service port packets traversing and getting replied by which device?
Regards,
Vishal Ranpariya
Technical Account Manager | Sophos Technical Support
Sophos Support Videos | Knowledge Base | @SophosSupport | Sign up for SMS Alerts |
If a post solves your question use the 'This helped me' link.
Command: tcpdump -ni any host 10.0.0.1 and port 22
82064 packets captured
95202 packets received by filter
13138 packets dropped by kernel
XGS2100_RL01_SFOS 19.5.1 MR-1-Build278#
I got this as result, after... 2 seconds runtime of the command. Crazy??
/cfs-file/__key/communityserver-discussions-components-files/126/dump1.txt
1st picture - SSH Package
2nd picture - Overview - with much "TCP Retransmission"
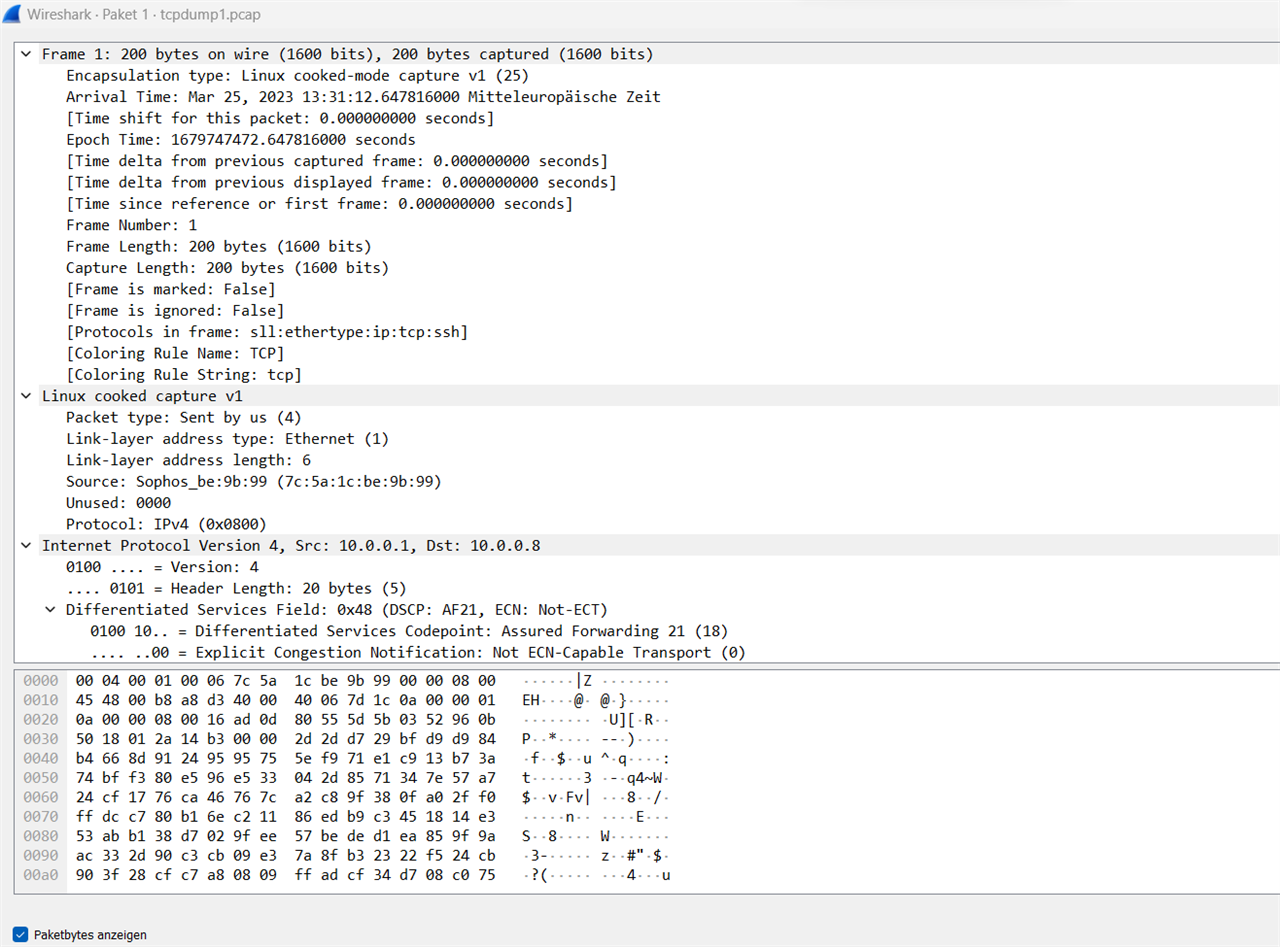
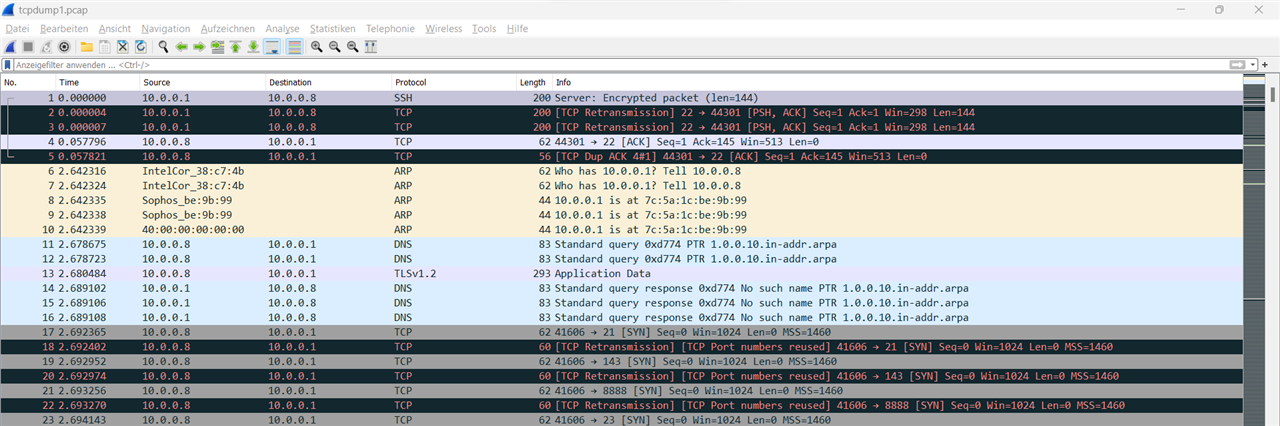
To solve the problem, should I maybe try to disable ipsec-acceleration and firewall-acceleration?
Disable IPsec Acceleration: https://docs.sophos.com/nsg/sophos-firewall/19.0/Help/en-us/webhelp/onlinehelp/CommandLineHelp/DeviceConsole/SystemCommands/index.html#command-ipsecacceleration
Disable Hardware Acceleration: https://docs.sophos.com/nsg/sophos-firewall/19.0/Help/en-us/webhelp/onlinehelp/CommandLineHelp/DeviceConsole/SystemCommands/index.html#firewall-acceleration
Hi Dennis Wauer: Here in the capture condition "host 10.0.0.1 and port 22" was used that will not give any other host IP if the firewall has forwarded the packet out to any other IP. Are there any changes to capture these packets and PCAP only on port 22 as per my previous comment?
Regards,
Vishal Ranpariya
Technical Account Manager | Sophos Technical Support
Sophos Support Videos | Knowledge Base | @SophosSupport | Sign up for SMS Alerts |
If a post solves your question use the 'This helped me' link.
Thanks for your reply and help.
When I use the command tcpdump -ni any host 10.0.0.1 and port 22, then I get:
14:42:44.743449 br0, OUT: IP 10.0.0.1.22 > 10.0.0.8.46445: Flags [P.], seq 17581104:17581424, ack 11761, win 1502, length 320
14:42:44.743450 Port4, OUT: IP 10.0.0.1.22 > 10.0.0.8.46445: Flags [P.], seq 17581104:17581424, ack 11761, win 1502, length 320
14:42:44.743452 oct0, OUT: IP 10.0.0.1.22 > 10.0.0.8.46445: Flags [P.], seq 17581104:17581424, ack 11761, win 1502, length 320
14:42:44.743470 br0, OUT: IP 10.0.0.1.22 > 10.0.0.8.46445: Flags [P.], seq 17581424:17581872, ack 11761, win 1502, length 448
14:42:44.743473 Port4, OUT: IP 10.0.0.1.22 > 10.0.0.8.46445: Flags [P.], seq 17581424:17581872, ack 11761, win 1502, length 448
14:42:44.743474 oct0, OUT: IP 10.0.0.1.22 > 10.0.0.8.46445: Flags [P.], seq 17581424:17581872, ack 11761, win 1502, length 448
14:42:44.743492 br0, OUT: IP 10.0.0.1.22 > 10.0.0.8.46445: Flags [P.], seq 17581872:17582320, ack 11761, win 1502, length 448
14:42:44.743495 Port4, OUT: IP 10.0.0.1.22 > 10.0.0.8.46445: Flags [P.], seq 17581872:17582320, ack 11761, win 1502, length 448
14:42:44.743495 oct0, OUT: IP 10.0.0.1.22 > 10.0.0.8.46445: Flags [P.], seq 17581872:17582320, ack 11761, win 1502, length 448
14:42:44.743514 br0, OUT: IP 10.0.0.1.22 > 10.0.0.8.46445: Flags [P.], seq 17582320:17582896, ack 11761, win 1502, length 576
14:42:44.743516 Port4, OUT: IP 10.0.0.1.22 > 10.0.0.8.46445: Flags [P.], seq 17582320:17582896, ack 11761, win 1502, length 576
14:42:44.743517 oct0, OUT: IP 10.0.0.1.22 > 10.0.0.8.46445: Flags [P.], seq 17582320:17582896, ack 11761, win 1502, length 576
14:42:44.743535 br0, OUT: IP 10.0.0.1.22 > 10.0.0.8.46445: Flags [P.], seq 17582896:17583344, ack 11761, win 1502, length 448
14:42:44.743537 Port4, OUT: IP 10.0.0.1.22 > 10.0.0.8.46445: Flags [P.], seq 17582896:17583344, ack 11761, win 1502, length 448
14:42:44.743538 oct0, OUT: IP 10.0.0.1.22 > 10.0.0.8.46445: Flags [P.], seq 17582896:17583344, ack 11761, win 1502, length 448
and muuuuuch of that and fast...
Hi Dennis Wauer I am able to see br0 in your last capture, Is there any bridge between LAN and WAN in your existing XGS?
Regards,
Vishal Ranpariya
Technical Account Manager | Sophos Technical Support
Sophos Support Videos | Knowledge Base | @SophosSupport | Sign up for SMS Alerts |
If a post solves your question use the 'This helped me' link.