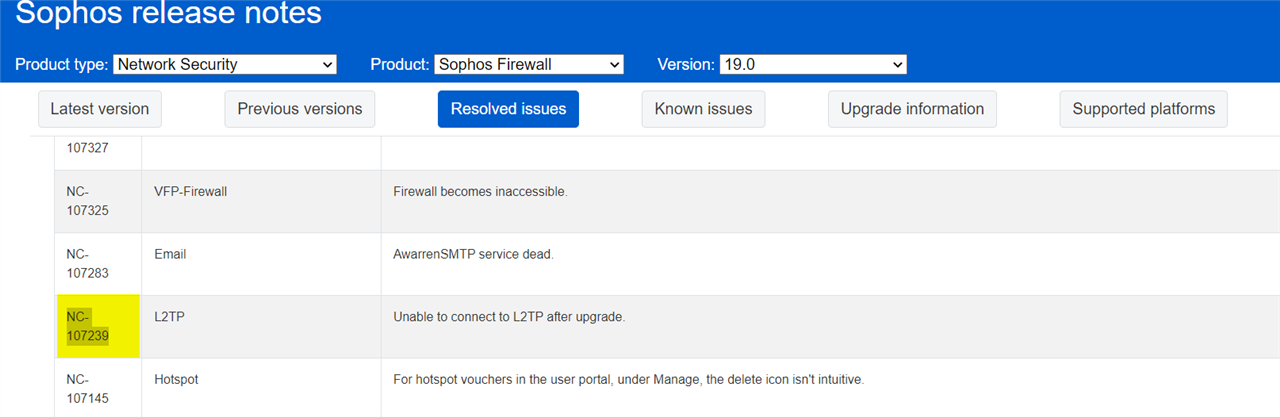
Hi,
after some testing I got the ip-sec part to connect but now I recive a error in l2tp.
"<l2t-1|94> received netlink error: Invalid argument (22)", I did some searching and it might be related to hw acceleration. But I don't know how to disable that in a SGX box or if it's actually the correct thing to do.
Whole log file
2023-03-24 12:48:35Z 20[NET] <94> received packet: from <client IP>[500] to <firewall IP>[500] (408 bytes)
2023-03-24 12:48:35Z 20[ENC] <94> parsed ID_PROT request 0 [ SA V V V V V V V V ]
2023-03-24 12:48:35Z 20[ENC] <94> received unknown vendor ID: 01:52:8b:bb:c0:06:96:12:18:49:ab:9a:1c:5b:2a:51:00:00:00:01
2023-03-24 12:48:35Z 20[IKE] <94> received MS NT5 ISAKMPOAKLEY vendor ID
2023-03-24 12:48:35Z 20[IKE] <94> received NAT-T (RFC 3947) vendor ID
2023-03-24 12:48:35Z 20[IKE] <94> received draft-ietf-ipsec-nat-t-ike-02\n vendor ID
2023-03-24 12:48:35Z 20[IKE] <94> received FRAGMENTATION vendor ID
2023-03-24 12:48:35Z 20[ENC] <94> received unknown vendor ID: fb:1d:e3:cd:f3:41:b7:ea:16:b7:e5:be:08:55:f1:20
2023-03-24 12:48:35Z 20[ENC] <94> received unknown vendor ID: 26:24:4d:38:ed:db:61:b3:17:2a:36:e3:d0:cf:b8:19
2023-03-24 12:48:35Z 20[ENC] <94> received unknown vendor ID: e3:a5:96:6a:76:37:9f:e7:07:22:82:31:e5:ce:86:52
2023-03-24 12:48:35Z 20[IKE] <94> <client IP> is initiating a Main Mode IKE_SA
2023-03-24 12:48:35Z 20[ENC] <94> generating ID_PROT response 0 [ SA V V V V V ]
2023-03-24 12:48:35Z 20[NET] <94> sending packet: from <firewall IP>[500] to <client IP>[500] (180 bytes)
2023-03-24 12:48:35Z 22[NET] <94> received packet: from <client IP>[500] to <firewall IP>[500] (196 bytes)
2023-03-24 12:48:35Z 22[ENC] <94> parsed ID_PROT request 0 [ KE No NAT-D NAT-D ]
2023-03-24 12:48:35Z 22[IKE] <94> remote host is behind NAT
2023-03-24 12:48:35Z 22[ENC] <94> generating ID_PROT response 0 [ KE No NAT-D NAT-D ]
2023-03-24 12:48:35Z 22[NET] <94> sending packet: from <firewall IP>[500] to <client IP>[500] (180 bytes)
2023-03-24 12:48:35Z 25[NET] <94> received packet: from <client IP>[4500] to <firewall IP>[4500] (76 bytes)
2023-03-24 12:48:35Z 25[ENC] <94> parsed ID_PROT request 0 [ ID HASH ]
2023-03-24 12:48:35Z 25[CFG] <94> looking for pre-shared key peer configs matching <firewall IP>...<client IP>[192.168.200.50]
2023-03-24 12:48:35Z 25[CFG] <94> selected peer config "l2t-1"
2023-03-24 12:48:35Z 25[IKE] <l2t-1|94> IKE_SA l2t-1[94] established between <firewall IP>[<firewall IP>]<client IP>[192.168.200.50]
2023-03-24 12:48:35Z 25[IKE] <l2t-1|94> scheduling reauthentication in 28324s
2023-03-24 12:48:35Z 25[IKE] <l2t-1|94> maximum IKE_SA lifetime 28684s
2023-03-24 12:48:35Z 25[ENC] <l2t-1|94> generating ID_PROT response 0 [ ID HASH ]
2023-03-24 12:48:35Z 25[NET] <l2t-1|94> sending packet: from <firewall IP>[4500] to <client IP>[4500] (76 bytes)
2023-03-24 12:48:35Z 19[NET] <l2t-1|94> received packet: from <client IP>[4500] to <firewall IP>[4500] (444bytes)
2023-03-24 12:48:35Z 19[ENC] <l2t-1|94> parsed QUICK_MODE request 1 [ HASH SA No ID ID NAT-OA NAT-OA ]
2023-03-24 12:48:36Z 19[IKE] <l2t-1|94> ### process_request invoking quick_mode_create
2023-03-24 12:48:36Z 19[IKE] <l2t-1|94> ### quick_mode_create: 0x2346ec0 config (nil)
2023-03-24 12:48:36Z 19[IKE] <l2t-1|94> ### process_r: 0x2346ec0 QM_INIT
2023-03-24 12:48:36Z 19[IKE] <l2t-1|94> expected IPComp proposal but peer did not send one, IPComp disabled
2023-03-24 12:48:36Z 19[IKE] <l2t-1|94> received 250000000 lifebytes, configured 0
2023-03-24 12:48:36Z 19[IKE] <l2t-1|94> ### build_r: 0x2346ec0 QM_INIT
2023-03-24 12:48:36Z 19[ENC] <l2t-1|94> generating QUICK_MODE response 1 [ HASH SA No ID ID NAT-OA NAT-OA ]
2023-03-24 12:48:36Z 19[NET] <l2t-1|94> sending packet: from <firewall IP>[4500] to <client IP>[4500] (204 bytes)
2023-03-24 12:48:36Z 16[NET] <l2t-1|94> received packet: from <client IP>[4500] to <firewall IP>[4500] (60 bytes)
2023-03-24 12:48:36Z 16[ENC] <l2t-1|94> parsed QUICK_MODE request 1 [ HASH ]
2023-03-24 12:48:36Z 16[IKE] <l2t-1|94> ### process_r: 0x2346ec0 QM_NEGOTIATED
2023-03-24 12:48:36Z 16[KNL] <l2t-1|94> ipsec_offload enabled
2023-03-24 12:48:36Z 16[KNL] <l2t-1|94> ipsec_offload interface Port2
2023-03-24 12:48:36Z 16[KNL] <l2t-1|94> received netlink error: Invalid argument (22)
2023-03-24 12:48:36Z 16[KNL] <l2t-1|94> unable to add SAD entry with SPI c5c3d3ff (FAILED)
2023-03-24 12:48:36Z 16[KNL] <l2t-1|94> ipsec_offload enabled
2023-03-24 12:48:36Z 16[KNL] <l2t-1|94> ipsec_offload interface Port2
2023-03-24 12:48:36Z 16[KNL] <l2t-1|94> received netlink error: Invalid argument (22)
2023-03-24 12:48:36Z 16[KNL] <l2t-1|94> unable to add SAD entry with SPI 4bec54be (FAILED)
2023-03-24 12:48:36Z 16[IKE] <l2t-1|94> unable to install inbound and outbound IPsec SA (SAD) in kernel
2023-03-24 12:48:36Z 16[IKE] <l2t-1|94> ### destroy: 0x2346ec0
2023-03-24 12:48:36Z 16[KNL] <l2t-1|94> deleting policy <firewall IP>/32[udp/1701] === <client IP>/32[udp/1701] out failed, not found
2023-03-24 12:48:36Z 16[KNL] <l2t-1|94> deleting policy <client IP>/32[udp/1701] === <firewall IP>/32[udp/1701] in failed, not found
2023-03-24 12:48:36Z 16[KNL] <l2t-1|94> deleting policy <firewall IP>/32[udp/1701] === <client IP>/32[udp/1701] out failed, not found
2023-03-24 12:48:36Z 16[IKE] <l2t-1|94> sending DELETE for ESP CHILD_SA with SPI 4bec54be
2023-03-24 12:48:36Z 16[ENC] <l2t-1|94> generating INFORMATIONAL_V1 request 382459208 [ HASH D ]
2023-03-24 12:48:36Z 16[NET] <l2t-1|94> sending packet: from <firewall IP>[4500] to <client IP>[4500] (76 bytes)
2023-03-24 12:49:11Z 06[NET] <l2t-1|94> received packet: from <client IP>[4500] to <firewall IP>[4500] (76 ytes)
2023-03-24 12:49:11Z 06[ENC] <l2t-1|94> parsed INFORMATIONAL_V1 request 3628773983 [ HASH D ]
2023-03-24 12:49:11Z 06[IKE] <l2t-1|94> received DELETE for ESP CHILD_SA with SPI 4bec54be
2023-03-24 12:49:11Z 06[IKE] <l2t-1|94> CHILD_SA not found, ignored
2023-03-24 12:49:11Z 28[NET] <l2t-1|94> received packet: from <client IP>[4500] to <firewall IP>[4500] (92 bytes)
2023-03-24 12:49:11Z 28[ENC] <l2t-1|94> parsed INFORMATIONAL_V1 request 4180688749 [ HASH D ]
2023-03-24 12:49:11Z 28[IKE] <l2t-1|94> received DELETE for IKE_SA l2t-1[94]
2023-03-24 12:49:11Z 28[IKE] <l2t-1|94> deleting IKE_SA l2t-1[94] between <firewall IP>[<firewall IP>]...<client IP>[192.168.200.50]
Thanks
Lennart
This thread was automatically locked due to age.